A complete guide to the Cyber Kill Chain
Cyberattacks can feel unpredictable, but most follow a pattern. Understanding attack progression can be the difference between stopping an attack early and responding after the damage is done. The Cyber Kill Chain® is one of the most widely used models for making sense of this process.
This guide explains both the classic and modern models of the Cyber Kill Chain, how it came to be, and how it fits into the broader landscape of modern cybersecurity.
What is the Cyber Kill Chain?
The Cyber Kill Chain is a cybersecurity framework that breaks down a cyberattack into distinct stages, from early planning to the final execution. The framework was developed by Lockheed Martin, drawing on the military concept of a “kill chain,” which describes the steps needed to identify a target and carry out an attack.
Why the Cyber Kill Chain still matters today
Despite major changes in the threat landscape since its introduction more than a decade ago, the Cyber Kill Chain continues to play a vital role in modern cybersecurity for several key reasons, including:
It provides a structured view of the attack lifecycle
By breaking complex cyberattacks into stages, the Cyber Kill Chain helps analysts and defenders visualize the progression of an attack. This helps teams anticipate attacker behavior and align defenses against threat progression.
It supports early detection and proactive defense
The Cyber Kill Chain gives defenders precise places to look for indicators of compromise and implement early warning systems. This is critical, as longer dwell time generally increases potential impact.
It guides incident response and threat analysis
During an active incident, the kill chain helps responders determine how far an attacker progressed, what capabilities may have been established, and which systems are likely affected. This allows teams to scope incidents more accurately, prioritize containment actions, and avoid both under-reacting and over-reacting.
It supports post-incident analysis and learning
After containment, the Cyber Kill Chain provides a framework for reconstructing what happened and identifying defensive gaps. Mapping an incident to kill chain stages helps teams understand which controls failed, where detection lagged, and how to improve future defenses.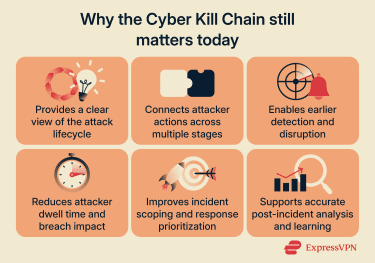
Who uses the Cyber Kill Chain?
The Cyber Kill Chain is used by different groups across cybersecurity, each applying it in practical ways depending on their role. These groups may include:
- Security operations centers (SOCs): These use the kill chain to monitor and triage alerts across different stages of an attack, helping them understand where an intrusion is occurring and prioritize responses based on attacker progress.
- Incident response and threat analysis teams: These teams rely on the kill chain as a shared reference when investigating breaches, mapping observed activity to specific stages to determine what has already happened, what may happen next, and which systems or data are most at risk.
- Threat intelligence teams: They use the kill chain to organize attacker behavior, connect individual tactics and techniques into a coherent narrative, and better understand how attacks develop over time.
- Educators and cybersecurity trainers: Trainers use the kill chain’s linear structure to explain how attacks unfold and why early-stage defenses matter.
The eight steps of the Cyber Kill Chain
The Cyber Kill Chain was originally defined with seven sequential steps, but many modern interpretations add an eighth step to better reflect how attacks unfold in real-world environments.
Reconnaissance: Identifying the target
Reconnaissance is the first stage of the Cyber Kill Chain, where attackers gather information about a potential target before launching a cyberattack. The goal, at this point, is to learn how a target operates, what systems are in use, and where weaknesses exist. Attackers typically carry out reconnaissance in two ways: passively and actively.
Passive reconnaissance focuses on collecting information without directly interacting with the target’s systems. This may include reviewing public websites, social media profiles, employee information, domain and infrastructure records, or other openly available data that reveals user behavior, technology choices, and operational patterns. Because it leaves little to no technical footprint, passive reconnaissance is difficult to detect and often occurs long before an attack becomes visible.
Active reconnaissance involves direct interaction with the target’s environment to gather more precise technical details. This can include scanning for open ports and exposed services, probing applications and login pages, or testing externally accessible infrastructure. While these techniques provide deeper insight into system configuration and potential vulnerabilities, they also increase the likelihood of early detection by security teams.
Weaponization: Preparing the malicious payload
During weaponization, attackers design and build the attack itself, based on what they learned during reconnaissance. They decide how they plan to exploit the target and what the malicious code will do once it runs. This includes selecting an exploit that matches the target’s software or behavior and pairing it with a payload capable of carrying out the attacker’s objective.
The key characteristic of this stage is that it’s highly customized, tailored to the target’s operating system, software stack, or security controls to increase the chances of success. It’s also one of the hardest stages to detect, as it happens before the attack is delivered.
Delivery: Transmitting the attack to the victim
In delivery, the prepared attack is sent to the target, typically relying on familiar channels like phishing emails, malicious links, infected USB drives, or compromised websites. The objective is to reduce suspicion long enough for the next stage to occur.
Because delivery requires the attack to pass through technical and human controls, it’s also one of the most defensible stages of the Cyber Kill Chain. Email gateways, web browsers, network controls, and security filters can often detect, block, or flag malicious content before a system is compromised.
Exploitation: Breaking into the system
Exploitation is the stage where a delivered attack successfully takes advantage of a weakness, technical or human, to break into a system or account. This may involve exploiting an unpatched vulnerability, abusing weak or reused credentials, or manipulating users through social engineering.
It may happen automatically or require user interaction, depending on how the attack was designed. Regardless, once exploitation succeeds, the attacker has an initial foothold inside the environment, enabling further actions in the stages that follow.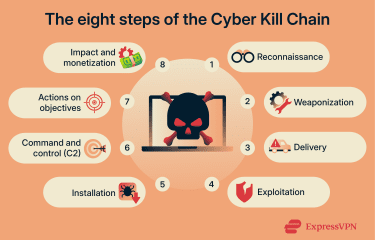
Installation: Establishing ongoing access
At this stage, attackers work to maintain access to a compromised system. The goal shifts to ensuring that access doesn’t disappear if the system restarts, credentials change, or security controls are updated.
To achieve this, attackers modify the environment so they can return reliably. This may involve adding persistence mechanisms, altering account permissions, or embedding access in ways that blend into normal system behavior. These changes often rely on legitimate system functions rather than overtly malicious files, making them difficult to detect.
Command and control (C2): Maintaining remote control
C2 is the stage where attackers establish a way to remotely manage compromised systems. At this point, attackers can direct activity on the system, deploy additional capabilities, move within the environment, and extract data.
To reduce the chance of detection, C2 traffic is often designed to blend into normal network behavior by using common protocols, encryption, or trusted services.
From a defensive perspective, C2 is a critical stage because it produces observable behavior. Unexpected outbound connections, unusual communication patterns, or systems checking in at regular intervals can all indicate attacker control. Disrupting these channels can effectively isolate compromised systems, limiting attacker activity even if earlier stages of the attack were successful.
Actions on objectives: Executing the final attack goals
This is the final stage in which attackers carry out the purpose of the intrusion. In the classic Cyber Kill Chain model, this represents the impact moment, the point at which the attack becomes visible to victims.
The specific objectives vary widely, but depending on the campaign, this may include data exfiltration, data encryption, data destruction, service disruption, or compromising additional systems such as suppliers or downstream partners. At this point, the attacker is actively using their access to harm the organization or advance the attack’s purpose.
Monetization: Achieving lasting damage or gain
Monetization is the eighth stage commonly added to the original Cyber Kill Chain to account for how attackers profit from successful intrusions. Rather than ending with technical impact alone, many modern attacks continue as threat actors attempt to generate income from the compromise. This may involve demanding ransom payments, selling stolen data, extorting victims with threats of disclosure, or otherwise leveraging access for financial gain.
Modern expansions (MITRE ATT&CK® and Unified Kill Chain)
As cyber threats have grown more complex, additional frameworks, like MITRE ATT&CK and the Unified Kill Chain, have emerged to address limitations in the Cyber Kill Chain.
The original Cyber Kill Chain models an attack as a short, mostly linear sequence that ends once objectives are reached. This works well for understanding external intrusion and early disruption, but it compresses everything that happens after access is gained.
ATT&CK expands on this by abandoning the idea of strict stages. Instead, it documents real attacker behaviors, such as credential abuse, lateral movement, privilege escalation, and persistence, and shows that attackers repeat and combine these actions as needed. This, essentially, fills in the behavioral detail that the kill chain leaves out.
The Unified Kill Chain changes the structure itself: where the original kill chain summarizes post-compromise activity, the Unified Kill Chain explicitly models it. It stretches the attack lifecycle into a longer sequence to account for prolonged internal activity, such as moving between systems, maintaining access, and operating over weeks or months.
Strengthening Cyber Kill Chain defenses with network security
From a defensive standpoint, network security plays a key role in disrupting multiple stages of the Cyber Kill Chain.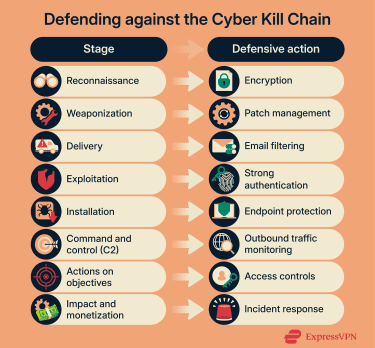
Protecting traffic in transit during reconnaissance and delivery
Early stages of the kill chain may depend on visibility into, and control over, network traffic. Attackers attempt to observe communications, impersonate trusted services, or interfere with content as it’s delivered to the target.
Controls that protect traffic in transit, such as encryption, authenticated connections, and secure routing, limit these opportunities. By denying passive visibility, enforcing endpoint trust, and preventing unauthorized modification of data in transit, defenders reduce both what attackers can learn during reconnaissance and how easily they can manipulate delivery paths. This hardens the boundary that attackers must cross before exploitation can occur.
Detecting exploitation and C2 through network monitoring
When attacks progress beyond delivery, network behavior often changes in observable ways. Successful exploitation and installation are frequently followed by outbound communication as compromised systems attempt to establish C2 channels.
Network monitoring focuses on identifying these deviations from normal behavior. Unexpected authentication attempts, unfamiliar outbound connections, unusual communication timing, or traffic to suspicious destinations can all signal active compromise. Detecting these patterns allows defenders to interrupt attacks before attackers fully establish control or act on their objectives.
Limiting post-exploitation impact with network segmentation
After gaining access, attackers commonly attempt to move laterally within the environment to reach additional systems or higher-value assets. Unrestricted internal connectivity makes this expansion fast and difficult to contain.
Network mapping and segmentation constrain this movement by dividing environments into smaller, isolated zones. By limiting which systems can communicate with one another, segmentation reduces the blast radius of a compromise and slows attacker progression, buying time for detection and response.
Disrupting C2 with DNS and traffic filtering
Most modern attacks rely on outbound communication to remain effective. C2 channels are used to issue instructions, receive stolen data, and adapt tactics as conditions change.
Domain Name System (DNS) and traffic filtering target this dependency by blocking communication with suspicious or untrusted destinations. When compromised systems cannot reach the attacker’s infrastructure, control is degraded or lost altogether. Disrupting these channels can prevent further damage.
How to implement the Cyber Kill Chain in your organization
Organizations get the most value from the Cyber Kill Chain when they use it as a coordination framework.
Building a proactive cyber defense strategy
Organizations can map common threats and attack scenarios to kill chain stages to identify where prevention, detection, or containment has the greatest effect.
This mapping helps organizations place controls earlier in the attack lifecycle, define escalation paths as attacks progress, and identify gaps where no control exists. Planning around stages makes defensive priorities explicit and reduces reliance on reactive measures after impact occurs.
Monitoring the Cyber Kill Chain in real time
Organizations can interpret security alerts by associating them with kill chain stages, and this association provides context about how far an attack has progressed.
Early-stage indicators point to probing or attempted access, and later-stage indicators point to confirmed compromise or active attacker control. Using this structure allows organizations to prioritize response actions based on progression, not alert volume.
Employee training and awareness programs
Human behavior plays a role in many attacks, so employee training is a critical part of kill chain defense. Organizations can use the Cyber Kill Chain to explain how attacks begin and escalate. This approach keeps training focused on behavior and impact, without requiring technical knowledge of tools or attack techniques.
FAQ: Common questions about the Cyber Kill Chain
What are the stages of the Cyber Kill Chain?
The classic Cyber Kill Chain® includes seven stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control (C2), and actions on objectives. Some modern frameworks add an eighth stage focused on impact and monetization.
Is the Cyber Kill Chain still used today?
Yes. While newer frameworks exist, the Cyber Kill Chain® is still widely used as a high-level model, particularly for education and planning.
How does the Cyber Kill Chain improve cybersecurity?
The Cyber Kill Chain® improves cybersecurity by breaking attacks into stages, helping defenders identify where controls can interrupt threats early.
What tools help monitor or break the Cyber Kill Chain?
Tools like network monitoring, Domain Name System (DNS) filtering, and endpoint protection can disrupt stages of an attack, especially during the exploitation and command and control (C2) stages.
Are there alternatives to the Cyber Kill Chain?
Yes, frameworks like MITRE ATT&CK® and the Unified Kill Chain expand on attacker behavior in more detail.
How often should organizations review their Cyber Kill Chain readiness?
Organizations should revisit their defenses regularly, as threats and security environments change rapidly.
Does the Cyber Kill Chain apply to individual users?
While individuals don’t formally implement the model, its principles help explain why protections like secure connections and encrypted traffic matter.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN