Understanding critical infrastructure security: A comprehensive overview
Power, water, healthcare, transportation, and communications are all vital in daily life. When these services are disrupted, the impact can spread quickly. Critical infrastructure security focuses on reducing the likelihood of such disruptions and on keeping essential systems operational or enabling rapid recovery.
This guide breaks down what critical infrastructure security involves, its practical implications, and how protection differs across environments.
What is critical infrastructure security?
Critical infrastructure security refers to the protections that safeguard the essential systems that keep society running.
In the U.S., the term "critical infrastructure" is defined in federal law as systems and assets (physical or virtual) so vital that their incapacity or destruction would have a debilitating impact on national security, the economy, public health, safety, or a combination of these.
Outside the U.S., governments and experts may use similar terms, sometimes with different names, to describe essential systems of this kind, such as the EU’s NIS2/CER frameworks or the UK’s Critical National Infrastructure (CNI) terminology.
Critical infrastructure security is not only about preventing incidents. It also covers the practical measures that allow services to continue operating or recover quickly. U.S. policy frames this as strengthening both security and resilience against physical and cyber threats.
Types of security in critical infrastructure
Critical infrastructure is exposed to many kinds of threats. Digital systems can be compromised, physical assets can be damaged, and operational processes can fail under pressure.
Because of that, security requires more than a single measure and is usually managed by multiple teams. Different layers must work together, each addressing a specific threat category.
Different kinds of critical infrastructure also require distinct security measures. While most infrastructure needs both digital and physical protection, the extent to which each is prioritized can vary.
Key types of security in critical infrastructure
Security can be broadly divided into three categories: IT cybersecurity, physical security, and operational technology (OT) / industrial control system (ICS) security. Here’s a quick overview highlighting the scope and purpose of each:
| Security type | What it focuses on | What it helps protect | Typical measures | Practical challenges |
| IT cybersecurity | Reducing risk to digital systems and networks | Business IT, identity and access management (IAM), data, and remote access pathways | Access controls, segmentation, monitoring, backups, and recovery planning | Security changes require careful testing and rollout to avoid downtime or unintended operational impact |
| Physical security | Preventing unauthorized access and reducing physical disruption | Facilities, equipment, control rooms, substations, data centers, and field sites | Perimeter security, controlled entry, surveillance, guards, and layered barriers | Physical access can bypass technical controls if sites aren’t protected |
| OT/ICS security | Protecting systems that monitor and control physical processes | ICS such as Supervisory Control and Data Acquisition (SCADA), distributed control systems (DCS), programmable logic controllers (PLCs), and supporting networks | Segmentation and controlled interconnections between enterprise IT and controlled networks, controlled access, and ongoing monitoring for anomalies | Availability and safety often outweigh convenience, and many systems run continuously |
Cybersecurity measures for critical infrastructure
Cybersecurity measures focus on protecting the digital systems that support the operation of essential services. This typically starts with IT networks, but in many sectors it also extends to the tools used to monitor, control, or support infrastructure services. While the exact scope varies by infrastructure type, virtually all critical sectors rely on digital components, from transportation systems to communications networks.
As more infrastructure systems rely on cloud-hosted tools and remote administration, securing those access paths becomes critical. Controls such as remote-access virtual private networks (VPNs) or zero-trust network access (ZTNA) are sometimes used to protect connections between users, systems, and services operating outside traditional network boundaries.
A key challenge is that critical infrastructure, especially OT/ICT environments, cannot always “stop and patch” the way a typical office network can. Uptime and safety matter, and some changes can introduce risk if they are rushed. That is why cybersecurity in these environments often starts with controls that reduce exposure and make abnormal activity easier to spot.
Some of the most common measures include:
- Network segmentation: Splitting networks into distinct zones limits how far an attacker can move if they gain access, making it harder for a compromise to spread from one area to another. This approach is foundational to reducing risk across complex environments.
- Authentication controls: Requiring multiple factors to verify user identities significantly reduces the risk that compromised credentials lead to unauthorized access. Many methods of two-factor authentication (2FA) exist, from hardware keys to specialized apps.
- Monitoring and visibility: Actively observing network traffic, system logs, and configuration changes helps teams spot unusual or suspicious behavior early. High visibility across systems enables faster threat detection and response.
- Vulnerability scanning and remediation: Regular scanning helps identify weaknesses before attackers exploit them. Proactively fixing these issues reduces exposure to common attacks and increases overall readiness.
- Backups and recovery planning: Backing up critical data and testing recovery procedures helps organizations restore operations quickly after an incident. In addition to minimizing downtime, this can prevent the loss of essential information.
Some threat activity can also be harder to trace or disrupt, with techniques like fast flux complicating blocking and takedown efforts. For those tasked with protecting infrastructure, the objective is to make intrusion harder, detect activity earlier, and limit the impact if an attacker does get through.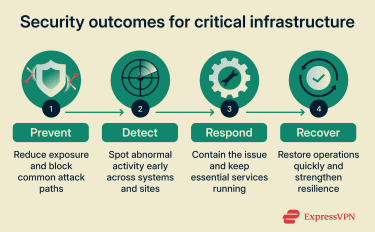
Physical security measures
Physical security focuses on protecting the facilities and equipment that critical infrastructure depends on. That includes facilities such as substations, control rooms, pumping stations, data centers, and transport hubs, along with the hardware in these places.
As with cybersecurity, the goal is straightforward: keep unauthorized people out, reduce the chance of interference, and limit damage if something goes wrong. In practice, that usually means controlling access to sensitive areas, protecting perimeters, maintaining surveillance, and training staff on how to respond when something looks off.
Physical protections also support resilience against non-malicious disruptions. Weather events, accidental damage, and equipment failure can disrupt operations just as easily as deliberate sabotage. Measures like backup power, environmental protections, and secure storage for spare components help reduce downtime when conditions are less predictable.
Because digital and physical systems are often connected, gaps on the physical side can weaken cybersecurity controls. If someone can reach key systems directly, many technical safeguards become easier to bypass. Physical security is thus considered an essential baseline requirement for protecting critical infrastructure of all kinds, from power stations and transport networks to communications and fiber-optic systems.
Operational technology (OT) / industrial control system (ICS) security
OT covers the hardware and software used to monitor and control physical processes. In critical infrastructure, this is often discussed as OT/ICS security. OT/ICS security can be considered a subset of cybersecurity, but it’s generally given its own category for practical reasons.
In critical infrastructure, OT/ICS commonly includes SCADA systems, DCS, and PLCs, which directly affect how equipment behaves in the real world.
OT/ICS environments operate under different constraints than traditional IT systems. Many components are designed to run continuously, sometimes for years. Because of that, security changes often need to be tested carefully and applied gradually. A measure that works well in an office network may not be safe to deploy in a live operational environment.
That reality shapes approaches to OT/ICS security. Instead of frequent system changes, the focus is often on stability, visibility, and controlled access. Knowing which devices are connected, restricting access to control networks, segmenting and tightly managing connections to business IT where necessary, and monitoring for abnormal behavior all help reduce risk.
Another challenge is convergence. As OT systems become more connected to business networks for monitoring, analytics, or remote maintenance, or connected sensors/devices, the attack surface expands.
In critical infrastructure, OT/ICS security is ultimately about balance. The aim is to protect systems from misuse or interference while keeping essential processes running safely and predictably.
Examples of critical infrastructure
Critical infrastructure covers a wide range of sectors that support daily life. Each sector has its own operational demands, risk profile, and security challenges, but all share the same baseline concern: disruption can affect large numbers of people and cause significant economic damage.
Energy sector
The energy sector underpins nearly every type of critical infrastructure. It includes electricity generation and transmission, oil and gas production, pipelines, refineries, and fuel distribution systems.
Because energy systems are highly interconnected, disruptions can quickly cascade into other sectors. Power outages can affect healthcare delivery, transportation networks, communications, and water treatment facilities. As grids modernize, security planning must increasingly account for distributed energy resources (DERs), including solar energy systems.
Energy systems also rely heavily on operational technology to manage real-time processes. Securing energy infrastructure environments means balancing availability, safety, and reliability while limiting exposure to threats that could interrupt supply or damage equipment.
Transportation sector
The transportation sector keeps people and goods moving, from roads and air travel to freight rail and ports. When transport systems are disrupted, the effects can spread fast because so many services depend on predictable logistics.
It's also a sector where cyber risk is taken seriously. U.S. government assessments have warned that cyberattacks can disrupt the transportation systems on which people and businesses rely.
For example, rail transit operators in the U.S. that receive federal assistance must certify that they have a process for developing, maintaining, and executing a plan to identify and reduce cybersecurity risks, highlighting the close link between resilience, continuity, and security.
In practice, security has to cover both the operational side (keeping services running safely) and the digital side (limiting exposure, detecting issues early, and recovering without extended downtime).
Healthcare sector
The healthcare sector is considered critical infrastructure because it supports essential medical services and patient care. When clinical systems go down, hospitals and clinics may have to delay care, switch to manual processes, or divert patients.
Healthcare systems typically involve a mix of public and private organizations, often spread across many independent providers. That fragmentation makes coordination and information sharing especially important for maintaining resilient services.
In the U.S., healthcare also has a clear security baseline for protecting electronic health information. The Health Insurance Portability and Accountability Act (HIPAA) Security Rule sets national standards and requires administrative, physical, and technical safeguards for electronic protected health information. Similar regulatory requirements exist in many other countries, though exact standards will vary.
On the threat side, U.S. health authorities warn that the sector continues to face increasingly sophisticated cyberattacks, including those that exploit complex, interconnected IT systems and network-connected medical technologies.
Best practices for critical infrastructure security
Most standard practices tend to look similar across sectors, even when the systems are different. A good starting point is to consider what could go wrong, what would matter most if it did, and where the biggest gaps are. From there, organizations can prioritize protections that reduce risk without creating unnecessary operational strain.
Assessment of vulnerabilities
Vulnerability assessments are critical to getting a clear picture of how secure the infrastructure truly is. These can determine which assets and services are most important, where exposure exists, and which gaps are most likely to be exploited.
Targeted assessments can have advantages over full audits. Instead of trying to grapple with an entire complex system at once, focusing on specific parts may yield deeper insights.
This kind of assessment work is meant to support prioritization. It gives decision-makers enough clarity to choose what to address first and what can wait.
That said, full audits are still necessary. They typically occur less frequently than targeted assessments, but it’s important that critical assets and functions are reviewed regularly.
Risk management frameworks
A risk management framework (RMF) provides a structured approach to assessing and managing risk. It outlines a repeatable process for analyzing the security situation and managing risk over time, rather than treating security as a one-time audit.
Risk management frameworks support consistent definitions of risk, evaluation of likelihood and impact, selection of safeguards, and tracking progress through ongoing monitoring and improvement.
Proactive incident response
A proactive approach assumes that incidents will happen at some point. The goal is to be ready before that moment arrives, not to figure things out under pressure.
For critical infrastructure, this usually means having clear plans, defined roles, and tested procedures in place in advance as part of an organization's security posture. When an incident occurs, teams should know how to detect it, who is responsible for decisions, and how to act without introducing new risks to ongoing operations.
Proactive response planning also focuses on containment and continuity. In many environments, especially those tied to physical processes, abruptly shutting down systems can be as damaging as the incident itself. A measured response helps isolate the issue, protect critical functions, and support speedy recovery.
Employee training and awareness programs
Technology is critical to security, but people still make small decisions that shape the overall picture. That is why training and awareness are often treated as core security practices and not optional extras.
For critical infrastructure, the goal is to ensure that the staff knows what safe behavior looks like in their roles, what to do when something out of the ordinary occurs, and how to avoid simple mistakes that can escalate into incidents.
Training also has to keep pace. Tactics change, systems change, and lessons from incidents should feed back into what teams are taught.
The strongest programs go further than a once-a-year module. They blend general awareness with role-based training for staff who touch sensitive systems, and they track completion to ensure gaps don't go unnoticed.
Building a cybersecurity culture
Cybersecurity culture refers to how employees actually engage with digital systems. This is naturally affected by training and procedures, but at its core, a culture reflects human day-to-day behavior. In a strong cybersecurity culture, staff will feel comfortable flagging suspicious activity and treat security as a core part of their jobs.
It also takes sustained effort. A culture that supports strong security does not emerge overnight, nor does it come from a single training cycle. It requires leadership support and a practical understanding of how teams work, what gets rewarded, and how issues are handled.
Collaborating for resilience
No single organization can secure critical infrastructure on its own. Critical infrastructure is often shared across public and private operators, making collaboration a practical requirement rather than just a good measure.
In practice, collaboration usually means two things: information sharing, so warnings move quickly to the people who can act on them, and coordinated action, so partners can align on planning, exercises, and response when incidents cross organizational boundaries.
In the U.S., programs like InfraGard link government and private-sector operators to facilitate information sharing and joint training.
Many sectors also use established channels, such as Information Sharing and Analysis Centers (ISACs), where organizations share cyber threat information with peers and, when appropriate, with government partners.
Emerging trends and future directions
Critical infrastructure does not stand still. Systems are being modernized, connected, and optimized, often to improve efficiency and reliability. At the same time, threat actors continue to develop new tools and tactics to deploy against key systems.
The role of AI in critical infrastructure
AI is increasingly being deployed in critical infrastructure environments, enabling practical applications such as monitoring, predictive maintenance, and decision-making. Done well, it can improve visibility and speed up response. If done poorly, it can introduce new safety and security risks into systems that support essential services.
Critical systems also increasingly rely on technologies outside traditional networks, including space-based services such as satellite communication and positioning (GPS), which bring their own resilience and security challenges.
Recent joint guidance from multiple national cybersecurity and security agencies warns that adopting AI in operational technology can introduce new risks to the environments in which it's integrated and to the critical functions it supports, emphasizing the need for governance, oversight, and planning.
The takeaway for critical infrastructure is straightforward. AI should not be treated like a plug-and-play upgrade. It needs a clear business case, careful integration, and ongoing monitoring. RMF can help teams consider trade-offs and trustworthiness as they design, deploy, and operate AI systems.
Threat landscape evolution
Threats to critical infrastructure continue to evolve, but the direction is consistent. Attackers often target systems that cannot tolerate downtime and environments where disruption can have real-world consequences.
Ransomware remains a major concern because it can take essential services offline and slow recovery even after systems are restored. Ransomware incidents can severely disrupt operations and leave organizations without the data they need to deliver mission-critical services.
At the same time, not all activity is designed to cause immediate disruption. Some campaigns focus on long-term access rather than immediate disruption. The goal is often to maintain a foothold in critical environments, positioning for future leverage or coordinated action.
Supply chain exposure is another growing risk. Critical infrastructure often depends on third-party software, vendors, and managed services. Weaknesses in those dependencies can give attackers indirect access to environments that would otherwise be difficult to reach.
Taken together, these patterns are why detection, containment, and recovery planning are now treated as core capabilities. The challenge is not just individual attacks but sustained or subtle activity that tests how well organizations can detect, isolate, and recover from ongoing threats.
FAQ: Common questions about critical infrastructure security
What are the three types of infrastructure security?
Infrastructure security is usually discussed across three areas: IT cybersecurity, physical security, and operational technology (OT) / industrial control system (ICS) security.
Cybersecurity focuses on protecting digital systems and networks. Physical security covers facilities, equipment, and access controls. OT/ICS security overlaps with both, protecting systems that monitor and control physical processes and the networks and access paths that support them.
How does critical infrastructure relate to national security?
Critical infrastructure supports essential services to national stability, including energy, healthcare, transportation, and communications. Disruptions can affect public safety, economic activity, and emergency response. Because of that impact, governments treat the protection of critical infrastructure as a national security priority.
What regulations and standards impact critical infrastructure security?
Rules vary by country, and many places don’t have one law that covers every critical sector. Instead, requirements usually come from a mix of sector-specific regulation, national cybersecurity/resilience frameworks, and standards.
In the U.S., there's no single federal law that governs all critical infrastructure. Requirements come from sector-specific rules, federal standards, and policy directives, for example, funding-linked cybersecurity requirements and healthcare rules for protecting electronic health information.
How can organizations improve their infrastructure resilience?
Organizations can adopt several practices to better secure critical infrastructure. These include conducting regular risk assessments, preparing response protocols, and mitigating human risk by running training sessions and fostering a strong security culture.
What are the latest threats to critical infrastructure?
Threats continue to evolve, but ransomware and state-sponsored cyber activity remain major concerns. These threats often target systems that cannot tolerate downtime and may aim to disrupt operations or establish long-term access for future leverage.
At the same time, increasing connectivity and modernization efforts can expand the attack surface if security does not keep pace. That makes detection, containment, and recovery just as important as prevention.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN