What is a data breach? How to safeguard your information
Data breaches are usually treated as single events, but their effects rarely stop at disclosure. Exposed data can resurface later, be reused in follow-up attacks, or trigger response and reporting requirements that extend well beyond the initial incident.
For both individuals and organizations, understanding what happens after exposure is as important as knowing how access first occurred. This article explains how data breaches are evaluated and handled in practice and what steps matter most after data exposure.
Please note: This information is for general educational purposes only and does not constitute legal advice. Breach response obligations vary by jurisdiction and incident context.
What is a data breach, and what it isn’t
A data breach is generally understood as any incident in which sensitive, protected, or confidential information is copied, transmitted, viewed, stolen, or used by an unauthorized person. An incident can affect personal, corporate, or institutional information in either electronic or physical form.
In privacy and compliance contexts, most notably under the European Union’s General Data Protection Regulation (GDPR), a personal data breach is broadly defined and may include the accidental or unlawful destruction, loss, alteration, or unauthorized disclosure or access to personal data.
These outcomes are often described (especially for personal data breaches) using the Confidentiality, Integrity, Availability (CIA) triad as:
- Confidentiality breaches: Unauthorized or accidental disclosure of, or access to, data.
- Integrity breaches: Unauthorized or accidental alteration of data.
- Availability breaches: Loss of access to data (temporary or permanent), including data destruction.
In some cases, cyberattacks like ransomware or phishing campaigns can result in data breaches, but only if they lead to unauthorized access or disclosure, data alteration, or loss of access to the data. So, not all hacks constitute breaches. Likewise, some data breaches (such as the physical theft of storage devices or hard-copy records) don’t involve hacks.
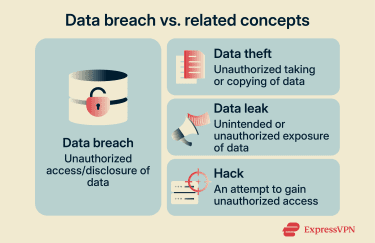
Data breach vs. data leak vs. hack vs. data theft
The term “data breach” is sometimes used interchangeably with related cybersecurity concepts. The following terms overlap but carry a few distinguishing characteristics.
- Data breach: The umbrella term for a security incident involving sensitive data, encompassing both intentional and accidental causes, external attackers and insiders, and various outcomes (theft, exposure, viewing, misuse, alteration, or loss of access).
- Data leak: Emphasizes exposure through the release or overexposure of data, often associated with misconfiguration, handling errors, or weak access controls. The term is also sometimes used for deliberate disclosures, depending on context.
- Hack: Describes a technique or action used to gain unauthorized access (for example, exploiting vulnerabilities or credentials). A hack can be part of a breach, but access alone doesn’t always imply data exposure or acquisition.
- Data theft: Emphasizes unauthorized acquisition of data (taking or copying). It can result from a hack or from the misuse of legitimate access by insiders.
Does encrypted data exposure still matter?
Data encryption scrambles sensitive data so it can’t be read without the decryption key, which reduces the impact of exposure. However, encrypted data exposure can still matter because encryption doesn’t eliminate risk.
If an attacker obtains the decryption keys, if keys are stored insecurely, or if encryption is implemented incorrectly, the encrypted data may still be readable. Likewise, physical theft or insider access can still lead to disclosure when the compromised device or account has access to the keys or can decrypt the data.
Encryption also may not remove breach response and reporting obligations. Encrypted (or otherwise de-identified) data can still be considered personal data where re-identification is reasonably possible (for example, if the decryption key is available), so legal obligations may still apply.
Read more: What is data privacy and why it matters: A complete guide
The data breach response lifecycle
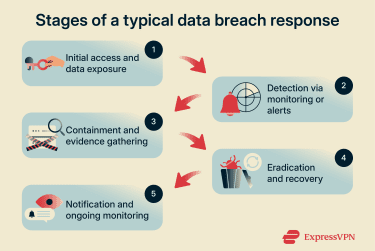
A data breach lifecycle often follows a sequence spanning from the initial incident through investigation, remediation, and (where required) notification.
- Intrusion and exfiltration: The initial incident may involve unauthorized access to a system or account or unintended exposure of data. Threat actors may identify and exploit security gaps to find restricted information. Exfiltration is the transfer of data out of an environment to an external destination. In some incidents, attackers also delete, encrypt, or corrupt data, affecting integrity and availability.
- Discovery and detection: Detection occurs when monitoring tools, audits, review processes, or external reports identify signs of unauthorized access, unusual data movement, or unexpected privilege changes. At this stage, the event may still be a suspected incident until access and impact are confirmed.
- Containment and investigation: Immediate containment limits further access and reduces ongoing damage. Investigation establishes how the intrusion occurred, the scope of affected systems, the specific data involved, and the likely impact. Logs and forensic evidence are preserved to support legal review and potential regulatory notification.
- Eradication and recovery: Eradication includes removing unauthorized access paths (such as malicious tools, compromised credentials, or persistence mechanisms). Recovery focuses on patching vulnerabilities and restoring systems and data to a known secure state, including from backups where available.
- Disclosure and post-breach monitoring: Disclosure involves notifying relevant stakeholders and, where required, regulators once the organization is aware that a breach has occurred, with updates as details are confirmed. Post-breach monitoring checks for repeat intrusions, misuse of exposed data, and gaps in remediation.
How do data breaches happen?
Several common factors (including technical, procedural, or human) can lead to data breaches:
1. Human mistakes and misconfigurations
Attackers often exploit everyday mistakes and weak configurations to access sensitive data. In many breaches, a human element (e.g., misdelivery, misconfiguration, or credential-related actions) is often involved.
Employees can expose information by sending it to the wrong recipient, storing it in unsecured locations, or granting access beyond their intended scope. Misconfigurations, such as publicly accessible cloud storage, excessive permissions, unsegmented networks, missing controls, or unencrypted sensitive data, can also expose data or enable unauthorized access.
2. Insider threats
Insider threats can originate from employees, contractors, trusted partners, or other authorized users who misuse access. Incidents can be malicious (intentional theft or sabotage) or non-malicious (unsafe handling or policy violations), but both can result in exposure or unauthorized use of data.
3. Stolen credentials and account compromise
Account compromise can occur when attackers use stolen credentials to access employee accounts. Once inside, attackers can use legitimate permissions to reach sensitive systems and data.
A common factor is reusing previously exposed passwords. In credential-stuffing attacks, cybercriminals automate login attempts using username–password pairs leaked from prior incidents and test them against other services.
4. Phishing and social engineering entry points
Social engineering exploits trust through impersonation or deception. Phishing and spear phishing attempts aim to trick recipients into sharing credentials, granting access, or running malicious content. These attacks can lead to breaches through account takeover or malware delivery, often starting with a fraudulent email or message.
5. Malware and ransomware incidents
Malware-enabled breaches occur when malicious code runs in an environment, enabling unauthorized access, data theft, or disruption. Spyware commonly focuses on covert monitoring and data capture, while ransomware can combine data theft with encryption to pressure organizations into paying.
6. Vulnerabilities and delayed patching
Unpatched software vulnerabilities can be exploited in operating systems, applications, APIs, or network services. After new vulnerabilities are disclosed, attackers may scan broadly for exposed systems. Delayed updates and unsupported software can create predictable entry points for compromise.
7. Lost or stolen devices
Data breaches can result from lost or stolen laptops, mobile devices, removable media, or backup drives that store sensitive information locally. Risk is higher when devices lack encryption, strong authentication, or appropriate access controls, or when shared credentials make access easier after theft.
8. Third-party and supply-chain breaches
Third-party breaches occur when partners or contracted providers with authorized access to data (for example, cloud services, security providers, or payment processors) experience incidents.
The compromise of one supplier can expose multiple connected parties when data is shared across organizations. These incidents complicate detection and response, as affected parties may learn of exposure through external notifications. According to Verizon’s 2025 Data Breach Investigations Report, breaches involving a third party doubled from 15% to 30% compared to the prior year.
Regulatory frameworks often place obligations on both controllers and processors, but the responsibilities differ between the parties.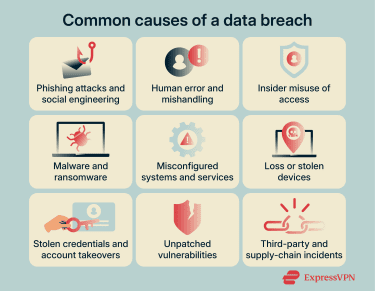
What information gets exposed in most data breaches
Most data breaches target sensitive end-user or corporate information, including:
- Login details and passwords: Usernames, email addresses, and passwords (sometimes hashed) tied to services such as cloud storage, banking, social media, and business accounts.
- Personal identifiers: Personally identifiable information (PII) can include any data that can help identify or contact a person, such as full names, addresses, Social Security numbers, phone numbers, or government IDs.
- Health information: For targeted healthcare providers, breached databases might expose patients’ medical diagnoses, prescription information, and treatment history.
- Payment data and billing information: Debit or credit card numbers, expiration dates, transaction records, and billing addresses.
- Business records and internal documents: Corporate breaches may expose internal documents such as contracts, operational records, and other proprietary data (sometimes including source code or trade secrets).
Why data breaches are so damaging
Data breaches are damaging because exposed information is valuable, often having financial or legal relevance. Personal identifiers and sensitive corporate data are also difficult to replace, meaning a breach can have long-lasting downstream effects on affected individuals.
Impact on individuals
For individuals, exposed identifiers, credentials, financial details, and other leaked data can be reused for identity theft, tax fraud, and insurance fraud, sometimes long after the original incident.
Comprehensive personal records can also be traded and resold on dark web markets, increasing the likelihood of repeated misuse beyond a single fraudulent event. In some cases, exposed data enables blackmail or coercion, particularly when sensitive personal or financial information is involved.
Impact on companies
For companies, data breaches combine direct financial loss with regulatory and operational consequences.
Following a data breach, providers face several business costs due to incident response, forensic investigations, and potential regulatory penalties depending on the jurisdiction and circumstances (if users’ personal data is involved). System downtime, restoration, and post-breach monitoring also increase the financial burden after an attack.
A business's long-term competitive advantage may suffer when valuable records and resources are exposed, stolen, or rendered unavailable during a ransomware incident. Following an event notification, breaches can erode end-user trust and business partnerships.
What to do if you’re affected by a data breach
Timely action reduces follow-up risks and limits the misuse of exposed data. Noteworthy measures include:
- Securing the affected accounts: Update passwords (and emails or phone numbers, where applicable) to stop unauthorized access. Keeping strong, unique passwords across accounts, reviewing account security settings, and enabling two-factor authentication (2FA) prevent secondary compromise.
- Deciding what to monitor based on what was exposed: The type and scope of the breach highlight whether high-risk accounts are vulnerable. A financial or identity data compromise requires heightened protection and ongoing monitoring of credit reports and bank statements. If the breach involved login data, monitoring typically focuses on suspicious sign-ins and access history.
- Watching for follow-up phishing and impersonation attempts: Attackers may reuse exposed contact details in wider social engineering campaigns. Signs of follow-up phishing attempts may include messages that create urgency, unusual requests to provide payment or login details, and messages that differ from a provider’s usual communications.
If follow-up attacks or impersonation scams are suspected, U.S. residents can report identity theft and related fraud to the Federal Trade Commission (FTC). For cybercrime (such as online scams or online theft), reports are commonly made to the FBI's Internet Crime Complaint Center (IC3), and suspected phishing incidents can also be reported to the Cybersecurity and Infrastructure Security Agency (CISA). In the European Union, reports are commonly made to local law enforcement for criminal matters or the relevant national Data Protection Authority (DPA).
Outside the U.S. and EU, reports are typically made to local law enforcement and the national data protection or privacy regulator (where one exists).
What can companies do to prevent breaches?
Established data handling best practices and controls help harden security, limit the impact of potential attacks, and support timely detection.
Security basics that reduce breach risk the most
Basic security controls address the most common causes of data breaches, such as misconfigured systems or workflows.
- Multi-factor authentication (MFA) and access control: MFA reduces the likelihood of account compromise when passwords are stolen or reused. Least-privilege controls and network segmentation limit resource access, containing the impact of account compromise and insider misuse.
- Encryption, backups, and secure storage: Encrypting sensitive data and maintaining offline or otherwise protected backups reduces exposure if systems are compromised. Backups also support recovery without paying ransoms, especially when they’re offline/protected and regularly tested.
- Monitoring and logging: Monitoring tools help detect suspicious activity across systems and networks. Examples include firewalls and intrusion prevention systems (IPS) for traffic control and security information and event management (SIEM) platforms for log collection, correlation, and alerting. Keeping activity logs also speeds incident documentation, response, and regulatory reporting.
Learn more: Read our guide on zero-trust architecture.
Reducing the blast radius when something goes wrong
Beyond risk management, an established incident response plan can limit the impact of an active breach, thereby reducing mitigation costs.
The FTC's Data Breach Response Guide and CISA guidance on ransomware-caused breaches outline key response steps and phases across the lifecycle of a security event.
When a compromise is detected, immediate isolation of affected servers, computers, and other endpoints (for example, disconnecting them from the network) can limit further unauthorized movement. This helps reduce the volume of data exfiltrated and the spread of malware across connected devices; powering down devices is typically a fallback when isolation isn’t possible. Updating access codes, credentials, and user permissions recovers compromised accounts.
Communication plans may include engaging forensic experts and contacting law enforcement to support documentation and a coordinated response. This helps preserve evidence for reporting, post‑incident analysis, and remediation planning.
Vendor and third-party security checks
Service providers and contractors with access to sensitive data or systems create potential endpoints for compromise, underscoring the importance of third-party security checks in risk management.
It’s a good practice for companies to evaluate which sensitive data their service providers can access, adjust privileges as needed, and assess key security risks and controls. In the event of a breach, it’s important to confirm that the corrective actions reported were implemented. Ongoing monitoring of third-party security practices reduces risks.
What a breach notification really means and how to read it
A breach notification is a formal disclosure that an organization has experienced a security incident that may have exposed or compromised sensitive information. Following a breach, notifications may be sent to regulatory authorities and affected individuals (where required), as well as to other stakeholders such as clients, contractors, or business partners.
Notifications are often delivered by email and/or written mail. Under the Health Insurance Portability and Accountability Act (HIPAA) Breach Notification Rule, notice to affected individuals is generally provided in writing by first-class mail or by email if the individual has agreed to receive notices electronically, subject to specific timing and substitute-notice rules. The notice typically summarizes what happened, the scope of the breach, the types of information involved, and the next steps in the organization’s response.
Many jurisdictions set breach-notification deadlines. Under the GDPR, controllers notify the supervisory authority without undue delay and, where feasible, within 72 hours of becoming aware of the breach, unless the breach is unlikely to create a risk. Individuals are notified without undue delay when the breach is likely to result in high risk.
What details should a good breach notice include
A proper breach notice is clear and practical, providing enough information for recipients to understand the incident and its likely impact.
- Date and timeline of the breach: When the incident occurred (if known) and when it was discovered, clarifying the likely exposure window.
- Description and cause of the event: What happened (and, where known, how it occurred), such as unauthorized access, system compromise, or accidental exposure.
- Types of data affected: Data categories like health information, financial data, PII, or login credentials help clarify the nature of the exposure.
- Likely impact and risks: The likely consequences for affected people and what misuse may look like.
- Measures taken to contain the breach: Steps taken to stop the incident and reduce further exposure.
- Steps that affected parties should take: Suggested follow-up actions, such as account monitoring, credential resets, or enrollment in identity protection services where offered.
- Contact information: A dedicated email, phone line, or web page for questions and incident-specific guidance.
The European Data Protection Board (EDPB) Guidelines provide further detail on when a breach must be reported, who must be notified, and what records must be kept.
How to tell if your data was actually involved
Breach notices often describe affected data types and total counts rather than identifying individual users. Some organizations provide additional ways to confirm individual impact, such as support channels or account dashboards.
Official channels (such as a known account portal or a verified support line) can help confirm a notification and reduce the risk of phishing. Follow-on suspicious messages, sign-in alerts, or unexpected account activity may appear after an incident when exposed data is misused.
Certain tools and services provide personalized signals. Have I Been Pwned aggregates many breach datasets and allows checks for whether an email address appears in the breaches it has loaded (though it can’t cover every breach). Some identity defense services monitor for signs of identity misuse and flag potential exposure indicators.
Read more: Massive social media breaches are exposing your private life.
When potential exposure still matters
Even when a breach notice indicates limited access, potential exposure can still matter. Partial or indirect exposure can increase future risk, including when attackers combine data from multiple incidents. This may include real details from older breaches combined with fabricated information to create synthetic identities used for fraud.
Read more: Why your old email is a goldmine for hackers.
FAQ: Common questions about data breaches
What happens when a company suffers a data breach?
When a company suffers a data breach, the provider must identify and contain the incident, assess which data was affected, and notify regulators and impacted individuals when required. Breaches involving personal or sensitive data may trigger mandatory disclosures, follow-up inquiries, and corrective security measures, depending on the jurisdiction and the incident's risk and impact.
How can I check if my data has been compromised in a breach?
Official breach notifications and account security alerts can indicate potential exposure following a breach, while signs of unauthorized activity can confirm misuse. Reviewing financial statements, tax records, and login histories helps identify misuse. Third-party tools and services may also flag unauthorized data use or exposure.
What steps should I take immediately after a breach notification?
Immediate steps advised after a breach include securing affected accounts, changing exposed credentials, enabling multi-factor authentication (MFA), and monitoring relevant records. If suspicious activity or impersonation attempts are detected, reports may be made to the relevant consumer protection, law enforcement/cybercrime, cybersecurity, or data protection authorities, depending on jurisdiction and the type of misuse.
Why is my iPhone saying my password appeared in a data leak?
iPhone’s saved-password security checks compare passwords in iCloud Keychain against a regularly updated list of passwords known to have appeared in leaks. If a password is flagged as “appeared in a data leak,” it means the password matches one found in known leak datasets, so any account using it may be at higher risk, even without visible signs of misuse.
Is a data breach the same as identity theft?
No, a data breach isn’t the same as identity theft. A data breach involves unauthorized access to or disclosure of information, while identity theft occurs when exposed data is actively used for fraud or impersonation.
What legal options exist after a data breach?
Legal options after a data breach typically include filing a complaint with the relevant privacy regulator, reporting associated fraud to law enforcement, and pursuing civil remedies (individual claims, class actions, or settlements) where the law allows and legally recognized harm can be shown.
Can a virtual private network (VPN) prevent a data breach?
A VPN can help protect data in transit (for example, on public Wi-Fi), but it can’t prevent most data breaches, which often involve service-side compromises or stolen credentials.
While it’s not part of a VPN’s core functionality, some providers also include identity defense or breach-monitoring features. For example, ExpressVPN’s ID Alerts can notify you if your personal information shows signs of exposure or misuse (availability varies by region).
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN