What you need to know about adversary-in-the-middle (AiTM) attacks

Adversary-in-the-middle (AiTM) attacks are a growing threat for large organizations because they can often monitor and record employees’ online communications without them knowing or take over their accounts by compromising active session data.
This guide offers an in-depth look at how AiTM attacks work, why they’re so dangerous, and how businesses and institutions can defend against them.
Note: Attempting to carry out or replicate an AiTM attack outside of authorized security testing is both illegal and unethical. This article's sole purpose is to aid readers in understanding the threat and strengthening their defenses.
What is an adversary-in-the-middle (AiTM) attack?
An AiTM attack, a modern form of the man-in-the-middle (MITM) attack, is a type of cyberattack where a malicious actor secretly positions themselves between a user and a legitimate service, such as a website, email provider, or cloud app, to control the communication between them.
Unlike passive interception, an AiTM attacker actively proxies the connection in real time. This allows the attacker to observe, modify, or inject data and actions within an active session, often without the user noticing.
How does an AiTM attack work?
AiTM attacks can occur in any scenario where an attacker is able to intercept and actively relay online communications. The steps below describe a typical AiTM attack.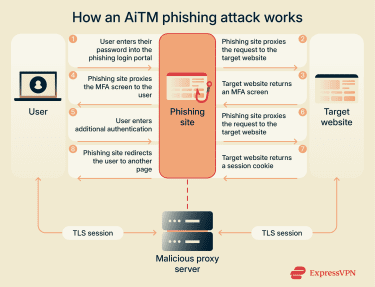
- The attacker inserts themselves into the communication path: Most often, the attacker uses a phishing link, but they may also rely on a compromised Domain Name System (DNS), unencrypted connections, malicious browser extensions, or infected endpoints.
- The cybercriminal proxies users’ data: The attacker’s server establishes live connections with both the victim and the website and relays requests and responses in real time so the interaction appears normal.
- The attacker observes or manipulates the active session: Because all traffic passes through the attacker, they can selectively capture credentials, session cookies, or authentication tokens, inject additional prompts, or perform actions using the victim’s authenticated session without alerting the user.
Tools and infrastructure AiTM attackers use
| Tool or component | What it is | How attackers use it |
| Lookalike domains and Transport Layer Security (TLS) certificates | Domains designed to resemble trusted brands, secured with valid HTTPS certificates | Make phishing and proxy sites appear legitimate by displaying familiar names and security indicators |
| Reverse-proxy phishing kits | Tools that sit between the victim and a legitimate service | Relay traffic in real time while capturing credentials, session cookies, and authentication tokens |
| Control panels and hosting | Web dashboards hosted on virtual private servers (VPS) or compromised servers | Allow attackers to monitor victims live, manage stolen sessions, and replay authenticated access |
| Browser-in-the-Browser (BitB) techniques | Scripts that simulate login pop-ups within a webpage | Increase realism of phishing pages, often used alongside AiTM proxies to reduce suspicion |
| Packet sniffers | Network monitoring tools | Used in network-level AiTM attacks to observe or record unencrypted traffic on insecure networks |
Types of AiTM attacks
AiTM attacks can be carried out in different ways, depending on where and how an attacker is able to insert themselves into a communication path. Some techniques operate at the network level, while others rely on redirecting or misrouting traffic.
Not every AiTM attack targets the same layer or asset. Grouping them by focus and method will help you understand the threat surface.
Network-layer AiTM attacks
These attacks sit close to your device. The attacker alters local network settings so traffic from connected devices flows through hardware they control. That position lets them eavesdrop on connections, monitor logins, or set up later session hijacking risks. Examples include:
- DNS spoofing or poisoning: The attacker manipulates DNS responses so traffic intended for a legitimate service is redirected to attacker-controlled infrastructure. This can enable interception or relaying of communications without obvious signs to the victim.
- Address Resolution Protocol (ARP) cache poisoning: The attacker falsifies address resolution data on a local network, convincing devices that the attacker’s system is the correct route to another host, such as the default gateway. Traffic is then routed through the attacker.
- Dynamic Host Configuration Protocol (DHCP) spoofing: The attacker supplies malicious network configuration settings, such as a rogue gateway or DNS server, causing victim traffic to flow through attacker-controlled systems.
- Rogue Wi-Fi access points: The attacker deploys a wireless network that mimics a legitimate access point. Once victims connect, all network traffic passes through hardware controlled by the attacker.
- Protocol downgrade attacks: In some network-layer AiTM scenarios, attackers attempt to force connections onto outdated or less secure protocols. For example, a secure HTTPS session may be downgraded to unencrypted HTTP traffic, enabling the attacker to observe or modify sensitive data in transit.
Endpoint-mediated AiTM attacks
In endpoint-mediated AiTM attacks, the attacker inserts themselves into the communication path by altering how the victim’s own device routes traffic, without manipulating DNS, Wi-Fi, or external network infrastructure.
In this scenario, malware or unauthorized system configuration forces the victim’s browser or operating system to route traffic through an attacker-controlled local or remote proxy. Once traffic is routed through this proxy, the attacker can intercept or relay communications transparently, even though the victim is connecting to legitimate websites and services.
Web-based AiTM phishing proxies
Here, the adversary sits on internet-facing infrastructure rather than a local router. They use phishing messages to steer victims to a malicious login URL backed by a reverse proxy. The reverse proxy communicates with the legitimate cloud service in real time, relaying authentication pages as the victim interacts with them. Because the login flow is proxied rather than imitated, authentication completes normally.
As authentication traffic passes through the proxy, the attacker captures credentials, multi-factor authentication (MFA) responses, and session cookies. These session tokens can then be replayed to access the victim’s account without reusing passwords or triggering MFA again.
Session-focused AiTM chains
Session hijacking is a related AiTM scenario in which an attacker takes control of an ongoing session and gains access to data or resources without initiating a new login. This attack type may allow cybercriminals to bypass advanced security protocols, like two-factor authentication (2FA) or MFA.
In practice, this often means replaying stolen cookies or tokens from an AiTM proxy, then creating mail rules, changing security options, or granting OAuth (the industry-standard protocol for authorization) access that keeps the account exposed long after the first phishing click.
AiTM combined with adjacent tricks
Some campaigns mix AiTM with other patterns, for example, BitB attacks, where scripts inside the browser simulate legitimate login windows, alongside ARP and DNS spoofing.
Others add BitB, which simulates single sign-on (SSO) pop-ups inside the page. These combinations strengthen deception around the AiTM infrastructure and make cloud account takeover threats harder to spot.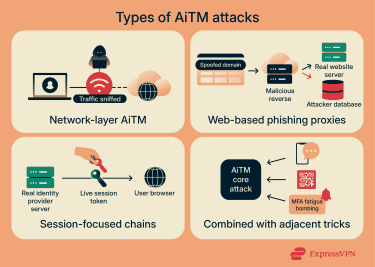
Real-world examples of AiTM attacks
Media reports and security researchers have documented several incidents involving AiTM attacks targeting large social news platforms, forums, and private organizations. Here are a few examples:
- AiTM attacks focusing on large organizations: Security researchers have noted multiple campaigns targeting large businesses that rely on identity management services, productivity platforms, and cloud storage.
- State-level interception of network traffic: In one documented case, a state intelligence agency intercepted data flows between major technology providers’ data centers. By gaining on-path access to communication links, the attacker was able to collect data in transit without the knowledge of either endpoint.
- Compromised certificate authority enabling AiTM: In one widely reported incident, attackers breached a trusted certificate authority and issued fraudulent Secure Sockets Layer (SSL) / Transport Layer Security (TLS) certificates for major domains including Google. Those bogus certificates were used in MITM attacks to intercept encrypted connections, allowing an intermediary to read or manipulate supposedly secure traffic until the certificates were revoked.
- On-path content injection by a network operator: In another reported incident, an internet service provider (ISP) modified web traffic passing through its network by injecting additional code into unencrypted HTTP responses. Because the modification occurred while the ISP was acting as an intermediary between users and websites, it involved direct manipulation of traffic in transit.
Typical targets and sectors at risk
AiTM attacks generally focus on high-value targets, particularly enterprise-grade organizations that provide critical services, manage large volumes of sensitive data, or handle financial transactions. Recent security reports show that the most at-risk public and private sectors include:
- Natural resources, energy, and environment.
- Construction, engineering, and manufacturing.
- Healthcare.
- Banking and finance.
- Government administration.
- Security, intelligence, and defence.
Why AiTM is a growing cybersecurity threat
AiTM attacks are increasingly concerning because of their sophistication: they’re difficult to detect and can quickly turn a single compromised login into widespread business impact.
Hard to detect
AiTM attacks can be difficult to detect without prior training or proper security measures in place. For example, an employee who connects to a company’s internal network over public Wi-Fi may be unaware that an attacker is monitoring their communications.
Additionally, AiTM campaigns that hijack sessions pose the same issue because, from a technical perspective, everything looks normal. They may add verification challenges, such as CAPTCHAs, to make automated security scans less effective.
Furthermore, attackers typically configure their proxy infrastructure to establish encrypted connections with both the victim and the legitimate website using TLS. This encryption helps obscure the attack’s activity, making it more difficult for network analysis tools to identify suspicious patterns.
Impacts on enterprises and individuals
Successful AiTM campaigns can cause severe damage. Cybercriminals may carry out financial fraud by manipulating victims into transferring payments to attacker-controlled accounts. They can also escalate access privileges to reach and exfiltrate sensitive data, which may later be sold for profit. In some cases, attackers generate new authentication tokens or modify security settings, helping them maintain access and evade detection.
In addition to financial harm, AiTM attacks can put employee and customer data at risk. Cybercriminals may intercept personal communications and steal identifying information, which can then be used in future phishing attempts or to facilitate identity theft.
How to detect and prevent AiTM phishing
Organizations can use advanced security solutions and detection methods to identify the early signs or stages of an AiTM attack. The sections below outline common warning signs of active threats, technical detection methods, and recommended security best practices.
Warning signs of possible attacks
Any of the following may indicate that an AiTM attack is in progress:
- Unexpected or repeated login prompts: Repeated requests to authenticate, especially when an active session should already exist, can indicate that authentication traffic is being relayed through an attacker-controlled intermediary.
- Authentication flows that behave differently: Login pages that load more slowly than usual, introduce extra redirects, or request MFA unexpectedly may indicate that the authentication process is being proxied in real time as part of an AiTM attack.
- Certificate or browser security warnings: TLS or certificate warnings on sites that are normally trusted may suggest that encrypted traffic is being intercepted or re-signed, a common requirement for attackers attempting to observe or modify protected communications.
- Unexpected redirects or subtle URL changes: Brief redirects through unfamiliar domains or small, unexpected changes in the address bar can signal that traffic is being routed through attacker-controlled infrastructure to establish an AiTM position.
- Successful logins followed by suspicious account activity: Normal-looking login success combined with later alerts about unfamiliar devices or locations may indicate that session tokens were captured during authentication and reused by an attacker without triggering additional login challenges.
- Frequent session terminations or logouts: Unexplained logouts or unusually short session lifetimes can result from session token interference, which may occur when tokens are intercepted or replayed by an attacker.
- Unusual network behavior on trusted connections: Changes in DNS settings, default gateways, or repeated network disruptions can indicate attempts to intercept or redirect traffic at the network level.
- Security tool or endpoint warnings: Alerts related to certificate substitution, DNS manipulation, or intercepted connections from security tooling often provide early indication of AiTM activity.
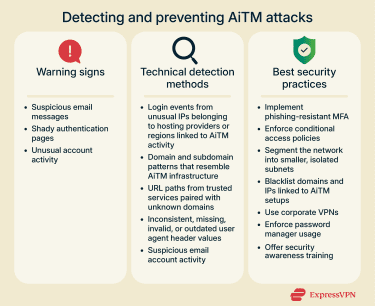
Technical detection methods
Organizations can use a mix of open-source or publicly available tools, endpoint detection and response (EDR) platforms, identity threat detection and response (ITDR) solutions, and network traffic monitoring to identify anomalous login patterns and suspicious account activity that may indicate an AiTM attack. Security teams should watch for any of the following when reviewing authentication logs, account activity, or network traffic:
- Login events from unusual IP addresses, such as hosting providers, distant countries, known proxy services, or regions associated with AiTM infrastructure.
- Domain or subdomain patterns that resemble known AiTM phishing setups or untrusted web servers.
- Unexpected URL paths from legitimate authentication services being paired with unfamiliar or unrecognized domain names.
- Irregular user agent (UA) headers, such as missing, invalid, or outdated values. AiTM servers may sometimes use hardcoded UA strings instead of forwarding the legitimate details from the user’s device.
- Inconsistencies in UA strings or source locations across multiple steps of the same authentication attempt.
- Anomalous email account activity, such as suspicious inbox rules or signs that messages are being accessed from unknown IPs or devices.
Protection best practices and tools
In addition to using comprehensive cybersecurity solutions that provide threat detection and protection, organizations should adopt the following security practices:
- Employ phishing-resistant MFA: Instead of relying on an additional verification step that could be intercepted, phishing-resistant MFA uses a unique cryptographic key generated between a user’s device and the service they are accessing. This key is used during login to confirm the legitimacy of both parties.
- Implement conditional access (CA) policies: These rules determine how users access data based on factors like identity, device health, and location. For example, the system may block an authentication attempt if it originates from an unfamiliar location, an unrecognized device, or outside standard business hours.
- Enforce subnetting: Dividing a network into smaller, isolated segments limits lateral movement if an attacker gains unauthorized access. This helps protect other parts of the network.
- Blacklist AiTM-associated domains and IPs: Prevent employees from interacting with known phishing URLs and ensure authentication attempts from malicious IP addresses are blocked.
- Avoid unencrypted networks: Require employees to avoid unsecured networks, such as public Wi-Fi, when accessing company data and accounts.
- Use corporate virtual private networks (VPNs): VPNs encrypt internet traffic and secure shared data, which can make it harder for malicious actors to monitor or interfere with corporate remote connections on unencrypted networks. Corporate VPNs are different from commercial VPNs, which improve security for individual users and small teams.
- Require password managers: These tools store all credentials in one place, protected by a single master password. They often autofill login fields on trusted sites, which may help users avoid entering their credentials into malicious authentication portals.
- Offer security awareness training: Provide regular training to help employees recognize phishing attempts, identify social engineering tactics, and report potential security threats or incidents.
AiTM-specific defense strategies
Core security practices help reduce exposure to cyber risks, including AiTM attacks. However, to effectively protect against these threats, organizations should also implement targeted measures such as zero-trust architecture, session token protection, and advanced email filtering and protection.
Zero-trust architecture
Zero-trust architecture is a security framework built on the principle that users and devices shouldn’t be inherently trusted. Instead, continuous identity verification is required to grant or maintain access to network data, servers, or services. The specific policies can vary, but they often include phishing-resistant MFA, strict CA rules, subnetting, real-time monitoring, automated threat responses, and strong encryption to protect data both at rest and in transit.
Given these principles, zero-trust security models help reduce exposure to AiTM threats and limit the potential damage of a successful attack. Because identity checks are performed continuously, access can be revoked as soon as an account exhibits abnormal or risky behavior.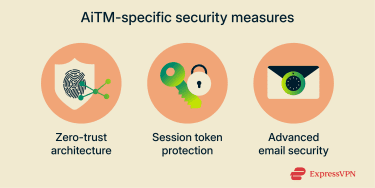
Session token protection
Some IAM platforms offer session token protection, a CA policy designed to help prevent session hijacking. When enabled, this feature cryptographically links a session token to the device it was generated on. As a result, even if a cybercriminal steals the token during an AiTM attack, they can’t use it from another device.
Network and transport security controls
Network-level protections reduce opportunities for attackers to redirect traffic through infrastructure they control. Secure wireless configurations, protection against rogue access points, and safeguards against unauthorized DNS, DHCP, or gateway changes limit the attacker’s ability to position themselves between devices and services. Enforcing encrypted transport and blocking protocol downgrade attempts further restrict what attackers can observe or modify if interception occurs.
Strict certificate validation and trust management also reduce the risk of unauthorized intermediaries intercepting encrypted traffic, ensuring that communications remain protected even on untrusted networks.
Endpoint configuration hardening
AiTM attacks can occur without visible network manipulation when attackers alter how a device routes traffic. Restricting changes to system and browser proxy settings, controlling browser extensions, and monitoring for unauthorized configuration changes reduce the risk of endpoint-mediated interception. Strong endpoint security controls and regular patching further limit the attacker’s ability to establish or persist an AiTM position on the device itself.
Advanced email security measures
AiTM attacks can begin with a phishing message, so implementing advanced email filtering is essential. These tools can detect, quarantine, or block potentially harmful emails, even when they appear to use legitimate URL shorteners or redirect services. When possible, organizations should adopt AI-powered filtering solutions that analyze message context and identify subtle warning signs.
Organizations should also use unified security platforms capable of detecting email threats commonly linked to AiTM activity. For example, these systems can generate alerts when messages contain malicious files or when email patterns match those of known phishing campaigns.
FAQ: Common questions about AiTM attacks
Can MFA stop AiTM phishing?
Regular multi-factor authentication (MFA) that verifies user identities through text messages or time-based codes can sometimes be bypassed by certain adversary-in-the-middle (AiTM) attacks, where malicious actors aim to hijack the authenticated session rather than break the MFA itself.
Are there open-source tools that help detect AiTM attacks?
Yes, several open-source and publicly available tools and datasets can help organizations detect adversary-in-the-middle (AiTM) threats. For example, security teams can use public lists of malicious IP addresses and domains to block access to harmful links or rely on website scanners to check for suspicious or unsafe URLs.
Can VPNs and password managers help?
VPNs and password managers don’t directly prevent adversary-in-the-middle (AiTM) attacks, but they can still reduce overall security risks. Corporate VPNs encrypt network traffic, which helps protect sensitive data. Password managers typically autofill credentials only on legitimate domains, which can help users notice suspicious or fake login pages when autofill does not occur.
What industries are most at risk?
Adversary-in-the-middle (AiTM) attacks generally target large private and public organizations. Security reports indicate that the most affected industries include energy, construction, engineering, and manufacturing. Other commonly impacted sectors include healthcare, finance, banking, government administration, environmental services, and defense.
Can VPNs protect against AiTM attacks?
VPNs don’t normally offer direct protection against all types of adversary-in-the-middle (AiTM) attacks, but they can help keep online communications safe when malicious actors try to monitor network traffic and capture readable data on unencrypted networks.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN