Supply chain attack: How it works and how to stay protected
Unlike some cyberattacks that try to break in directly, supply chain attacks exploit trusted components involved in building, delivering, or operating software and services, allowing attackers to gain access through legitimate workflows and integrations.
In this article, we’ll explain how supply chain attacks happen, why cybercriminals exploit supply chains, common techniques used, and the measures organizations can take to guard against them.
Note: Any attempt to replicate or deploy a supply chain attack outside of authorized security testing is illegal and unethical. The information in this article is provided solely to support awareness of the threat and help strengthen defensive security practices.
What is a supply chain attack?
A supply chain attack is a type of cyberattack where attackers compromise a trusted component in the software or service delivery process and use that access to infiltrate downstream organizations.
In a software and services context, the supply chain refers to all the components, tools, and services that contribute to building, delivering, and running an application or system. This includes software dependencies, development and build tools, deployment pipelines, internal platforms, and external vendors or service providers.
Because these components are trusted and integrated into production environments by design, a compromise can be propagated through normal software delivery or service operations without appearing suspicious.
How these attacks work
Many supply chain attacks follow a similar pattern, even though the technical details vary:
- Initial compromise: Attackers gain access to a trusted organization or system in the supply chain by exploiting vulnerabilities using methods such as tailgating, phishing employees, or using stolen credentials.
- Introduction of malicious code or abuse of trusted access: After gaining access, attackers either insert malicious code into software, build artifacts, updates, or shared components, or abuse existing permissions to access downstream environments directly. This can occur during development, build, or post-deployment operations.
- Distribution through trusted channels: The affected software, component, or service reaches downstream systems through legitimate mechanisms such as software builds, updates, integrations, or existing service access.
- Impact on downstream organizations: Once the compromise reaches customer systems, attackers can steal data, deploy ransomware, monitor activity, or move within internal networks.
Why supply chains are a high-value target
Attackers target supply chains because they allow a single compromise to have an outsized impact. Instead of attacking organizations one at a time, attackers focus on upstream components that many systems depend on, allowing a single breach to affect multiple downstream environments.
Beyond scale, supply chain components often provide deep levels of access. Software, services, and infrastructure tools typically require elevated permissions to function correctly. If attackers gain control of a compromised component, update, or service, they may inherit those same privileges, which in some cases includes administrative access across critical systems.
The complexity of modern supply chains further increases risk. Organizations rely on a mix of internal tools, third-party services, subcontractors, and integrated platforms, but often lack full visibility into how each component is secured. This makes weaknesses harder to identify and easier for attackers to exploit.
Detection and response are often slower as well. When malicious activity originates upstream or outside an organization’s direct control, teams may struggle to trace the source, understand the scope of exposure, and coordinate remediation across multiple affected parties.
Common vectors and techniques in supply chain attacks
There’s no single way supply chain attacks happen. Attackers typically target upstream components in the supply chain, where a single compromise can propagate to many downstream systems through existing trust relationships. Here are some of the most common paths they take.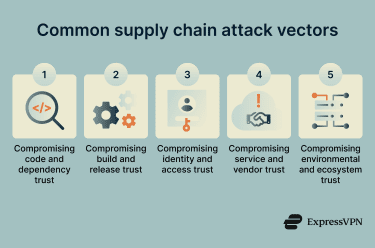
Compromising code and dependency trust
Attackers target third-party dependencies that developers routinely include in their applications, including libraries, packages, frameworks, software development kits (SDKs), and other shared components obtained from public or private repositories.
Common techniques include typosquatting, where a malicious dependency is published under a name similar to a legitimate one, and dependency confusion, where build systems are manipulated into pulling a public package instead of an intended private dependency. In some cases, attackers compromise maintainers’ accounts to distribute malicious updates through otherwise trusted libraries or components.
Compromising build and release trust
Continuous integration/continuous delivery (CI/CD) pipelines are the systems developers use to write, test, and release software. They automate the building, testing, and deployment of software, and as such, have direct access to source code, build artifacts, signing keys, and deployment environments.
If a pipeline is compromised, the attacker could introduce malicious code during the build process, before the software is released. Because the resulting artifacts are generated and distributed through trusted, automated workflows, malicious changes can be difficult to detect downstream.
Compromising identity and access trust
Developer endpoints are another common entry point into the supply chain. Developers often have access to source code repositories, internal tools, and credentials required to build or deploy software.
By compromising a developer’s workstation, attackers can inject malicious code into projects or gain access to systems that support the build and release process. Since activity originates from a legitimate internal account or device, these compromises can bypass many security controls.
Compromising service and vendor trust
Many businesses depend on external services, such as cloud platforms, email providers, or file-transfer tools, to run day-to-day operations. These services often require persistent access to internal systems, APIs, or sensitive data.
If one of those services is compromised, attackers can use it to access systems or intercept sensitive data. This risk is higher when the service handles authentication, configuration management, remote administration, or software distribution, since those functions typically require elevated privileges.
Compromising environmental and ecosystem trust
These attacks target websites or online tools that developers or IT staff frequently visit. Instead of attacking the developers directly, attackers compromise a trusted site, like a code repository, plugin hub, or documentation portal.
When a developer visits the site, malware could be downloaded to their machine. If successful, it can give attackers a foothold in the development process or a wider network. Because the infection comes from a “safe” site, it’s easier to overlook.
Real-world examples of supply chain attacks
Supply chain attacks have happened to major companies and governments. Here are some of the most significant cyberattacks related to supply chain infiltration.
- Compromised software updates: In 2020, security researchers found that attackers had inserted malicious code into a legitimate software update for an IT monitoring product, which was then distributed to customers through official update channels.
- Managed file transfer exploitation: In 2023, investigations found attackers exploited a previously unknown vulnerability in a widely used managed file transfer (MFT) application. The vulnerability was used to deploy web shells and exfiltrate data from affected systems across multiple sectors.
- Remote management tool abuse: In 2021, reports described that attackers exploited vulnerabilities in remote management software commonly used by managed service providers. The compromise allowed ransomware to be deployed to downstream customer environments through trusted administrative access.
- Compromised application installers: In 2023, investigators confirmed that a legitimate desktop application installer had been compromised, resulting in the distribution of malicious code to users who downloaded the software through official channels.
How to detect supply chain compromises
Detecting a supply chain compromise is challenging because malicious activity often originates from trusted components and follows normal operational paths. Traditional perimeter-based alerts may not trigger, so detection relies on identifying subtle signs of abnormal behavior and verifying the integrity of systems and code over time.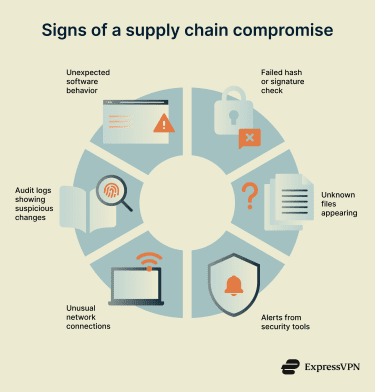
Early warning signs
Supply chain attacks often hide in plain sight. But before serious damage is done, there are usually subtle clues:
- Unexpected software behavior: If a trusted software suddenly starts doing unusual things, such as connecting to odd domains, using large amounts of processing power, or prompting unusual alerts, that could be a red flag.
- Integrity check failures: Many software downloads include a hash or digital signature, a kind of fingerprint that proves the file hasn’t been tampered with. If the hash or signature doesn’t match what the developer or vendor provides, it’s a sign that the file may have been altered or replaced with something malicious.
- New or unknown files: If new executables or scripts appear on a build server or developer machine without explanation, that could be a red flag. Seeing unknown programs pop up uninvited is a classic malware sign.
- Alerts from security tools: Advanced security systems like security information and event management (SIEM) and endpoint detection and response (EDR) track activity across your network and devices. If one of these tools raises an alert about your development environment or a recent software update, take it seriously.
Monitoring software behavior and anomalies
Because supply chain attacks often rely on legitimate software, monitoring how systems behave over time allows you to establish a baseline that makes it easier to spot deviations.
Examples of anomalous behavior include unexpected outbound connections from CI/CD servers, unusual API calls, or software accessing resources outside its normal role. Even small anomalies can point to a larger issue when they involve trusted systems.
Audit trails and code integrity checks
Audit trails help confirm when and where changes occurred. Logs from source control, build pipelines, and deployment tools provide critical context during an investigation. Maintaining an up-to-date Software Bill of Materials (SBOM) makes it easier to trace which components were used in each build. This can quickly narrow the scope when a compromised dependency or tool is identified.
Code signing and integrity checks add another layer of assurance by helping confirm that builds and updates have not been altered prior to execution. Unexpected signature failures can signal that a change needs further investigation before software is executed or distributed.
How to reduce the risk of supply chain attacks
Lowering the risk of supply chain attacks involves tightening security at every link of the chain. Common measures may include some of the following:
Secure the software development lifecycle
The software development lifecycle (SDLC) is an important place to reduce supply chain risk, since vulnerabilities could be introduced at multiple stages from development through deployment.
In practice, organizations often focus on protecting source code repositories, securing CI/CD pipelines, and limiting the tools and dependencies used in production workflows.
Tracking and reviewing changes to code or build configurations can help create an auditable record of how software is produced. Teams may also use practices such as code reviews, automated security checks, and additional approvals for critical pipeline changes to reduce the likelihood that a single compromised account can alter production software.
Vendor risk assessment and due diligence
Vendors and service providers extend the supply chain beyond an organization’s own infrastructure, which means vendor security practices can influence overall supply chain risk.
Organizations that understand how vendors handle vulnerabilities, patching, and incident response are better positioned to manage risk. Looking beyond direct vendors to their subcontractors and service dependencies also helps surface hidden exposure that would otherwise go unnoticed.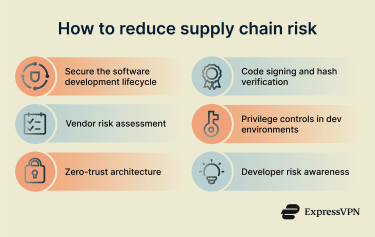
Use zero-trust architecture
A zero-trust architecture can help limit the impact of a supply chain compromise by removing implicit trust between systems. Rather than assuming internal components are safe, access is evaluated continuously, which often includes measures such as network segmentation and authentication requirements between systems and services.
Zero trust also relies on the principle of least privilege, which includes giving build servers and service accounts only the permissions they absolutely need. In many environments, CI/CD systems are designed to access credentials or keys only when needed, which can help contain the effects of a compromise and reduce how far it can spread.
Use code signing and hash verification
Code signing and hash verification are commonly used to help confirm the integrity of software before it is installed or executed. Digital signatures on OS packages, drivers, and libraries can indicate whether software has been altered since it was released.
For internally developed software, automated signing processes are often used to support integrity checks and detect unexpected changes. For third-party software, comparing file hashes or signature information against values published by the vendor can help identify files that may have been modified or replaced.
Restrict privileges in dev environments
Development and build systems often end up with more access than they need. Developers and CI tools rarely require full administrative rights, and limiting those privileges can help reduce the impact of a compromise.
Approaches such as isolating build steps, separating developer machines from critical systems, and minimizing the use of long-lived credentials in CI/CD pipelines can help contain how far a breach spreads if one occurs.
Train developers on supply chain risks
Developers are often the first to notice when something feels off. Familiarity with common supply chain risks, such as compromised dependencies, suspicious updates, or social engineering, can help them spot issues early.
Teams that routinely question unexpected library changes, verify sources before adopting new tools, and report anomalies help reduce the risk of supply chain issues.
FAQ: Common questions about supply chain attacks
How are supply chain attacks different from direct hacks?
Direct hacks typically target a company’s own systems. Supply chain attacks exploit weaknesses somewhere in the broader network of tools, vendors, or services the company relies on. That could mean compromised software libraries, infected hardware, hijacked cloud platforms, or even tampered developer tools.
How can small companies protect their pipelines?
Small teams often focus on foundational controls that improve visibility and limit access within their build environments. Common approaches include using version control, narrowing access to build tools, and applying additional authentication where appropriate.
Attention to where dependencies come from, how updates are validated, and how anomalies are handled can also help reduce the risk of malicious code entering a pipeline, even in smaller teams.
What are the warning signs of compromise?
Watch for mismatched file hashes, unusual system behavior, strange network traffic, or unexpected changes in your code or tools. Alerts from antivirus or monitoring systems, especially after a software update, may warrant further investigation.
Is using a VPN enough to protect software supply chains?
No. A virtual private network (VPN) protects your online traffic from third parties, but it doesn’t inspect the software you download or use. Protecting your supply chain typically involves secure coding practices, verified dependencies, access controls, and ongoing monitoring, not just encrypted connections.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN