What makes polymorphic viruses so hard to detect?
Polymorphic viruses are designed to evade security tools while infecting devices, systems, and networks. The first step to avoiding these threats is understanding how they work, and this article provides an in-depth overview of polymorphic viruses, how to detect them, and the best ways to prevent infections.
Note: Trying to replicate polymorphic viruses outside authorized testing environments is unethical, dangerous, and illegal. The information in this guide is only meant to help readers understand polymorphic threats so they can better protect against them.
What is a polymorphic virus?
A polymorphic virus is malicious software that makes changes to the appearance of its code while the core algorithm remains the same to preserve the virus’s original function. The transformation happens each time the virus spreads, ensuring every new version appears different. This helps it avoid standard antivirus detection, which often relies on static signatures to identify malicious software.
Polymorphic virus vs. polymorphic malware
These two terms are often used interchangeably, but there’s an important distinction. Malware is a broad term for malicious software, while a virus is a specific type of malware that spreads by making copies of itself as it infects devices or networks.
A polymorphic virus repeatedly changes parts of its code to produce different-looking variants, helping it evade signature-based detection while continuing to self-replicate. Polymorphic malware is a wider category that includes polymorphic viruses as well as other types of malware, such as trojans or ransomware, which can also modify their code.
Examples of polymorphic malware
Security researchers, law enforcement agencies, and media outlets have documented several incidents involving polymorphic malware. Here are a few notable examples:
- Attack that compromised millions of computers: According to media reports, the malware spread through phishing emails citing weather disasters. The messages contained a malicious attachment that delivered the infection, which had polymorphic capabilities that allowed it to regularly change its signature.
- Ransomware infection with polymorphic traits: Security researchers identified what’s believed to be the first instance of polymorphic ransomware. In addition to encrypting victims’ files for ransom, it generated unique versions of itself to avoid detection.
- Polymorphic downloader that installed other malware: One news report claims this malware infected up to 100,000 computers per day and required coordinated action between multiple international law enforcement agencies to shut it down.
- Large-scale cybercrime operation: A notorious malware strain combined multiple malicious capabilities, including polymorphic code, to steal sensitive data. According to a press release, it was only disrupted through coordinated global action involving law enforcement and judicial authorities.
How does a polymorphic virus work?
A polymorphic virus changes its form using a mutation engine, which is a software component embedded within the virus itself. This engine allows the virus to automatically modify, encrypt, or restructure its payload, ensuring each new infection looks different. To stay undetected, a polymorphic virus may use one or more of the following techniques:
- Code obfuscation: Alters its code to make analysis more difficult without affecting its core malicious functionality. This can include reordering instructions or inserting meaningless code solely to change the file’s binary appearance.
- Variable encryption: Uses different cryptographic keys for each new infection. This causes the virus to spread using varying encryption patterns, which makes signature-based detection harder.
- Executional adaptation: Modifies how it executes, allowing the virus to blend in with normal system processes and interfere with behavior-based detection tools.
In practice, these changes are often small, just enough to alter the binary signature and evade simple pattern-matching, while keeping the underlying behavior and functionality the same.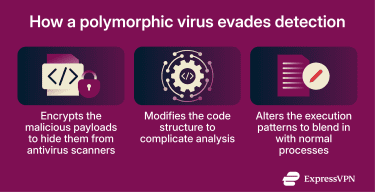
How polymorphic viruses spread
Polymorphic viruses typically infect systems through the following methods:
- Large-scale phishing campaigns: Cybercriminals may send hundreds or thousands of emails, with each message carrying a slightly different version of the virus to evade security scanners.
- Drive-by downloads: Fake or compromised websites can automatically trigger malicious downloads, infecting users’ devices with polymorphic viruses without a clear warning.
- Malicious ads: Cybercriminals may embed polymorphic code into fake online ads, with each ad impression delivering a mutated payload to the visitor’s system.
- Infected files: Malicious actors may disguise polymorphic viruses as free utilities, fake updates, or cracked apps, which activate once users run the downloaded program.
- Physical media: Attackers may deliver infections through removable media, such as USB drives, with the virus mutating as it spreads across systems.
Polymorphic virus vs. metamorphic virus
Both polymorphic and metamorphic viruses aim to avoid signature-based antivirus detection by ensuring each new infection looks different. A polymorphic virus only changes how its code looks, while a metamorphic virus rewrites the actual internal code structure to appear differently.
What can a polymorphic virus do?
Once it infects a device, a polymorphic virus starts mutating and self-replicating to compromise the system and spread to other devices or networks without being detected. Depending on its core purpose, it may also steal sensitive data or install additional malware.
Evading antivirus detection
Polymorphic viruses can evade antivirus detection that relies on signatures. Signature-based antivirus software works by matching known byte patterns from previously identified malware.
Polymorphic malware breaks that approach by making sure those byte patterns don’t stay consistent. Each new copy is typically re-encrypted or re-packed with a different key and a slightly different decryptor or loader, so the file’s raw bytes change. This makes signature-only detection unreliable, since the fingerprint it depends on keeps shifting.
Spreading malware payloads
A polymorphic virus is often used as a delivery mechanism for other threats. Instead of being the main payload itself, it may act as a dropper or loader that infects a system and then downloads or installs additional malware. The polymorphic part helps the malware keep changing its appearance so it can spread further and avoid detection while it delivers the real payload.
How to detect a polymorphic virus
Polymorphic viruses can evade traditional signature-based detection, so heuristic and behavior-based tools must be used instead. Fortunately, many modern antivirus programs offer such detection features. Enterprise-grade organizations may also employ next-generation antivirus (NGAV) platforms for enhanced protection.
Learn more: If you think your device may be compromised and want to confirm it, check our list of common signs of computer infection.
Heuristic and behavior-based detection
Unlike signature-based detection, heuristic analysis doesn’t rely on databases of known malware fingerprints. Instead, it focuses on suspicious patterns, behaviors, and characteristics that deviate from normal system, app, and network activity. Heuristic and behavior-based detection typically does the following:
- Tracks behavior: Monitors system processes and app activity for actions that deviate from the norm.
- Detects anomalies: Identifies behavior that doesn’t align with standard system activity.
- Evaluates rules: Uses advanced rules and algorithms to determine whether detected patterns and actions are malicious.
- Generates scores: Rates how likely a behavior is to be malicious.
- Creates alerts: Flags patterns and actions that exceed a risk threshold for further review.
This high level of dynamic detection helps security programs that use heuristic and behavior-based analysis more easily spot advanced threats, including polymorphic viruses.
Next-generation antivirus (NGAV) protection
NGAV protection is a modern, often cloud-based cybersecurity solution that combines behavior-based detection with machine learning and AI. These platforms continuously monitor files, events, and processes for potentially malicious patterns.
NGAV services also establish baselines of normal activity across devices, networks, and user identities, which makes subtle deviations easier to detect. Advanced AI algorithms can then correlate signals from multiple telemetry sources, such as logs, authentication events, and file activity. This continuous monitoring and learning process allows NGAV platforms to adapt to emerging polymorphic threats.
Challenges in identifying polymorphic malware
Some security tools, including modern programs, may still struggle to detect polymorphic malware for one or more of the following reasons: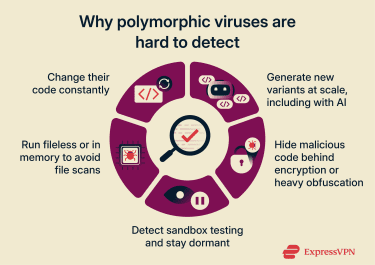
- Continuous code mutations: Security programs that rely mainly on signature databases can’t keep up with the sheer number of unique signatures polymorphic malware generates, especially since a single code mutation can instantly render an existing signature ineffective.
- AI-driven infections: Attackers may use AI tools to speed up parts of the malware development process and lower the barrier to producing polymorphic variants.
- Static analysis inefficiencies: Malicious payloads are often hidden behind encrypted or heavily obfuscated code. Security tools that rely on static analysis and ignore the obfuscation layer may fail to detect polymorphic threats.
- Sandbox detection: Advanced malware can detect when it’s being executed in a virtualized or isolated analysis environment. This is a long-running arms race: sandbox tools try to hide signs of analysis, while malware looks for even small hints and may stay dormant or delay execution until it reaches a real target system.
- Fileless malware behavior: Some polymorphic threats avoid creating malicious files on a device’s disk and instead abuse system tools or run entirely in memory. This helps them bypass security programs that only scan files for signs of infection.
How to prevent polymorphic virus infections
Protecting your devices and network from polymorphic and other malicious threats generally means keeping everything up to date, using advanced antivirus protection, and taking steps to improve your overall online security.
Keeping systems and software up to date
Outdated operating systems and applications can create security gaps that cybercriminals exploit to deliver malware, including polymorphic viruses. Keep your system and programs updated to the latest versions to apply security patches and remove apps that no longer receive support. To reduce the risk of errors, enable automatic updates wherever possible.
Using advanced malware protection
Protect your device using an antivirus with heuristic and behavior-based detection. Many modern security programs offer this level of protection and also scan system memory, not just files. After installing the software, make sure real-time protection stays enabled at all times so threats don’t slip through. Also, scheduling regular full system scans, such as once a week, adds an extra layer of protection.
Note: Organizations may consider integrating NGAV solutions into their existing cybersecurity frameworks, as these services offer more comprehensive protection for safeguarding company data.
Practicing safe browsing and email habits
The most effective way to prevent polymorphic virus infections, along with other malicious threats, is to avoid them in the first place. You can practice safe browsing and improve your email security by doing the following:
- Be wary of free offers: Unless it’s a legitimate service or trial, avoid websites that promise free access to paid products. Downloading anything from these pages can trigger malware infections.
- Use an ad blocker: Cybercriminals often rely on malvertising, which delivers malicious code through ads. Blocking ads from loading in the first place helps reduce your exposure to these risks.
- Block and report suspicious emails: These messages may include harmful links or dangerous attachments that expose you to polymorphic threats. Common signs an email isn’t safe include unknown senders, urgent or threatening language, and poor spelling or grammar.

Educating yourself on cyber threats
Understanding how malicious software works and how cybercriminals deploy it can help you avoid potential infections. For example, learning the common signs of malware may help you spot an infection early and act before it causes serious damage. Likewise, becoming familiar with phishing attacks makes it easier to recognize suspicious messages that could lead to an infection.
FAQ: Common questions about polymorphic viruses
What’s the difference between a polymorphic and a metamorphic virus?
Both polymorphic and metamorphic viruses evade standard antivirus detection, but they do it in different ways. A polymorphic threat typically uses encryption to hide its malicious payload and may also make minor code changes. A metamorphic virus, on the other hand, doesn’t rely on encryption and instead fully rewrites its code with each new iteration.
Are polymorphic viruses still a threat today?
Yes, but cybercriminals more often use polymorphic malware in modern attacks. This broader category includes polymorphic viruses as well as other types of malware with polymorphic traits that can compromise sensitive data, such as trojans, ransomware, or keyloggers.
Can polymorphic viruses be completely removed?
Yes, but this typically requires advanced antivirus protection that uses heuristic and behavior-based detection. This approach looks for suspicious behaviors and patterns rather than relying on fixed signatures. Standard signature-based scanning usually can’t fully remove a polymorphic threat because its code keeps changing.
Why are polymorphic viruses hard to detect?
Polymorphic viruses are hard to detect because they evade traditional, signature-based antivirus tools. They rely on a mutation engine to encrypt their malicious payload and make ongoing changes to their code, so each version looks different.
How serious is a polymorphic virus infection?
A polymorphic virus infection can be a serious threat because it can evade traditional, signature-based antivirus detection while spreading to other devices or networks. Depending on how it’s programmed, it may also steal sensitive data or deliver additional malware, such as ransomware or trojans.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN