What is 128-bit encryption, and is it still secure in 2026?

128-bit encryption remains a cornerstone of online security, protecting everything from virtual private network (VPN) traffic to mobile apps. It’s widely used and has never been reported to have been cracked. But with ongoing advances in computing power, there are real concerns about its future.
This article explores what 128-bit encryption is, how it works, how it compares to 256-bit encryption, and whether it still offers enough protection.
What does 128-bit encryption mean?
When we talk about 128-bit encryption, we’re usually referring to Advanced Encryption Standard (AES), a widely used and highly secure encryption algorithm.
Encryption is the process of converting readable data into an unreadable format, making it unintelligible to anyone without the correct key. This protects information from unauthorized access.
The “128-bit” part refers to the length of the cryptographic key used to scramble and unscramble the data. The longer the key, the more possible combinations exist. With 128-bit encryption, there are 2¹²⁸ possible key combinations, making it virtually impossible for an unauthorized party to guess the correct one and break the encryption.
How does 128-bit encryption work?
Encryption relies on ciphers, algorithms that dictate exactly how data is altered to become unreadable.
AES is a symmetric encryption algorithm, meaning the same cipher key is used for encryption and decryption. In contrast, asymmetric encryption methods use a unique key for each of these tasks.
Here’s how 128-bit AES encryption works in practice:
- The algorithm takes readable data and the 128-bit cipher key as input.
- The data is altered according to a series of complex mathematical operations. The key determines how difficult it is to decrypt the data, while the cipher dictates the overall complexity of the encryption.
- Output is produced in the form of seemingly random data.
- When the same key is applied to output data, the equations run in reverse, restoring the data to its original, readable form.
When was 128-bit encryption first adopted?
128-bit encryption became a formal standard in 2001, when the U.S. National Institute of Standards and Technology (NIST) approved AES to replace its predecessor, the Data Encryption Standard (DES). AES was created to support cipher key lengths of 128, 192, and 256 bits. The adoption of AES marked the first time 128-bit encryption was widely used as the default method for securing sensitive data.
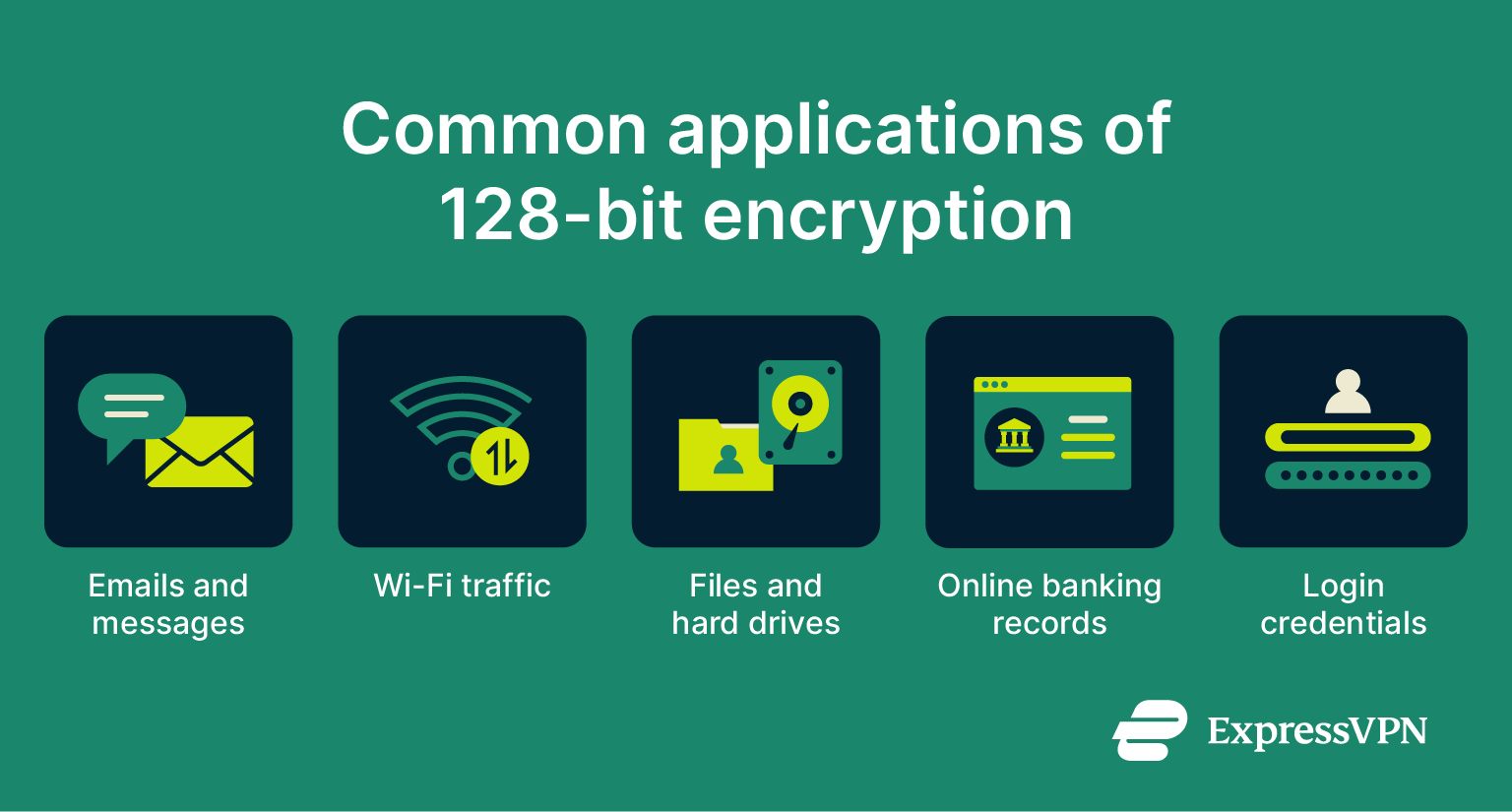
What types of data are typically encrypted with 128-bit algorithms?
128-bit encryption is used to secure a wide variety of data in many different fields and settings, from passwords and patient records to private communication and everyday web browsing. Here are some of the most common applications:
- Personally identifiable information: This includes sensitive personal data such as names, addresses, Social Security numbers, and credit card details.
- Financial data: Transactions and account information in banking, payment processing, and online commerce.
- Communication data: Emails, instant messages, and voice-over-IP calls often rely on 128-bit encryption to maintain confidentiality.
- Data stored on devices: Many systems use 128-bit encryption to protect data that’s backed up or stored on hard drives, USB drives, and mobile devices. Full-disk encryption tools and file encryption software sometimes default to or support 128-bit encryption.
- Wi-Fi network traffic: Protocols like Wi-Fi Protected Access 2 (WPA2), which secure wireless networks, use 128-bit AES encryption to thwart potential eavesdroppers.
- Government and enterprise data: A lot of public and private organizations use 128-bit encryption to secure internal communications, VPN tunnels, and other kinds of information.
Where is 128-bit encryption used today?
128-bit encryption is used in many settings, including:
- VPNs: While most leading VPNs rely on 256-bit AES, many offer the option to scale back to 128-bit for personal performance tweaking.
- HTTPS: HTTPS websites rely on the Transport Layer Security (TLS) protocol, which supports both 128-bit and 256-bit encryption to secure the data exchanged between browsers and servers. In practice, 128-bit AES is often favored because it provides sufficient security and better performance.
- Mobile and Internet of Things (IoT) devices: Mobile devices have limited resources compared to desktops, making 128-bit keys more appealing. Mobile apps and IoT devices often prefer 128-bit encryption in order to optimize battery life and save processing power.
- Legacy systems: Many systems continue to support 128-bit protocols alongside newer alternatives so as to avoid creating compatibility issues with older hardware and software.
What standards define 128-bit encryption?
128-bit AES encryption was formally defined by the Federal Information Processing Standards (FIPS) Publication 197, a standard published by NIST. It lays out how symmetric block ciphers should operate and provides other technical specifications. To be more exact, FIPS 197 states that data blocks should be 128 bits and that cipher keys should be either 128, 192, or 256 bits.
Several widely used standards incorporate 128-bit encryption as a key pillar. Examples include:
- Secure Sockets Layer (SSL): An early protocol for encrypting data sent between devices and servers. SSL does support 128-bit encryption, but the entire protocol is now deprecated. The term SSL is sometimes used as a term of convenience, but the underlying protocol has been replaced by TLS (e.g., SSL VPNs actually use TLS).
- Transport Layer Security (TLS): The modern replacement for SSL. As mentioned above, TLS is what most websites use now to secure HTTPS connections. TLS supports various encryption methods, including 128-bit keys.
How secure is 128-bit encryption?
128-bit encryption remains a foundational security measure used worldwide, but ongoing advances in computing and emerging technologies raise important questions about its long-term resilience.
Has 128-bit encryption been cracked or broken?
128-bit encryption has a long history of use and has been rigorously tested and probed by cryptographers worldwide. To date, no reliable method has been found to crack or break it.
128-bit AES encryption is highly resilient against brute force attacks, so even the most powerful modern computers have been unable to break it. At the time of writing this article, it would take longer than the projected lifespan of the universe to brute force a 128-bit AES cipher key with a standard computer.
How 128-bit security holds up against quantum threats
While 128-bit security remains effectively unbreakable by classical computers, the future of encryption faces a new challenge: quantum computing. In theory, sufficiently powerful quantum computers could render it vulnerable. Quantum computers with these capabilities don’t exist yet, but experts believe they could emerge within the next two decades.
Quantum computers could threaten 128-bit security in two primary ways. First, they could accelerate brute-force key searches for symmetric encryption algorithms like 128-bit AES through a technique known as Grover’s algorithm, halving the effective key strength.
The second quantum threat comes from a technique called Shor’s algorithm, which could be exponentially faster at solving the mathematical problems underpinning widely used asymmetric encryption methods such as Rivest–Shamir–Adleman (RSA) and elliptic curve cryptography (ECC). This matters because many real-world systems use a combination of encryption types: symmetric encryption protects the actual data, while asymmetric encryption establishes the secure connection.
Upgrading 128-bit security for the quantum era
The potential threat of quantum computing has driven the development of post-quantum cryptography (PQC), encryption methods designed to resist quantum attacks.
For symmetric encryption, strengthening quantum resilience largely comes down to key length. To protect from brute-force attacks, some experts recommend moving from 128-bit to 256-bit AES. The longer key increases the number of possible combinations exponentially, making brute-force attacks, including those accelerated by quantum computing, unfeasible. An alternative is switching from AES to ChaCha20, a symmetric encryption algorithm that uses key lengths of 256-bits.
For both 128-bit and 256-bit security, it’s also important to quantum-proof the key exchange, the process by which two parties securely agree on a shared secret cryptographic key used to encrypt and decrypt the data. This is critical because, even if the symmetric encryption itself is strong, a compromised key exchange could allow an attacker to intercept or manipulate the secure session.
Key exchange is typically handled by asymmetric encryption algorithms. However, as noted above, classical methods such as RSA and ECC aren’t quantum resistant. Therefore, it’s necessary to move to post-quantum key-exchange mechanisms, such as Module-Lattice-based Key Encapsulation Mechanism (ML-KEM), which rely on mathematical problems that are difficult to solve even for quantum computers.
As an example of a quantum-safe approach, ExpressVPN relies exclusively on 256-bit AES encryption (by default) and ChaCha20 (can be selected manually) for symmetric encryption. And for key exchange, it has implemented hybrid post-quantum protocols combining ML-KEM with classical algorithms in both its proprietary Lightway protocol and its customized WireGuard implementation. This ensures that the connection remains secure even if one method is eventually broken by quantum computers.
Should you trust 128-bit encryption in 2026?
128-bit encryption is currently a reliable security standard with a proven track record. However, the quantum future may not be far off, and 128-bit encryption can’t be considered quantum-safe. Quantum computers could halve the effective strength of symmetric encryption and also compromise the key exchange handled by classical asymmetric algorithms.
For this reason, organizations preparing for the future should upgrade to symmetric encryption with longer key lengths, such as 256-bit AES or ChaCha20, which are more resistant to brute-force attacks. It’s also critical that they implement quantum-secure key-exchange methods, such as ML-KEM.
On the flip side, individuals should be mindful of whether the tools they use are quantum resilient. VPNs, messaging apps, and other services that rely on encryption may eventually be vulnerable if they depend on 128-bit security or classical-only key exchange. Choosing services that have adopted 256-bit encryption and quantum-safe key-exchange protocols can help protect personal data and ensure long-term security.
FAQ: Common questions about 128-bit encryption
Is 128-bit encryption good enough?
128-bit encryption is secure and sufficient for most everyday uses. It provides strong protection against current threats and offers advantages in speed and compatibility compared with longer key lengths.
However, it’s not quantum-safe; future advances in quantum computing could render it vulnerable, and organizations already need to start preparing for this possibility. For highly sensitive data or long-term protection, it’s recommended to upgrade to 256-bit Advanced Encryption Standard (AES) or ChaCha20 and pair it with quantum-resistant key exchange methods, such as Module Lattice–based Key Encapsulation Mechanism (ML-KEM).
What is the difference between 256-bit AES and 128-bit encryption?
The main difference is the key length. 256-bit Advanced Encryption Standard (AES) uses a longer key. This makes it more secure and better suited for protecting highly sensitive or long-term data. However, many people still choose to use 128-bit encryption because it remains unbroken today and comes with other advantages, like faster performance and lower energy consumption.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN