How can you protect your home computer?

Many people underestimate how vulnerable their personal computers are. Without corporate-grade defenses or IT oversight, home setups are often easy targets. At the same time, new trends such as malware-as-a-service (MaaS) and AI-generated phishing have made cyberattacks more frequent, convincing, and difficult to detect.
Unfortunately, home computer protection isn’t as simple as just installing the most popular antivirus. True cybersecurity requires a layered approach, from monitoring the dark web for leaked information to being cautious about the USB devices you plug into your computer. Even small details like your router settings can have a real impact on your digital security.
In this article, you’ll learn about common threats to watch out for and practical steps to strengthen your defenses. You’ll also find a curated list of cybersecurity news sources and tools to help you stay on top of the latest trends and assess your security.
Essential steps to protect your home computer
Taking proactive measures is key to protecting against common cyber threats. Here are five effective steps that can strengthen your overall computer security.
Keep your operating system and software updated
Regularly updating your OS and applications is one of the simplest yet most effective (and often overlooked) ways to protect your computer. Updates often include critical security patches that fix newly discovered vulnerabilities, which cybercriminals may otherwise exploit to gain access, install malware, or steal data.
To stay protected, enable automatic updates wherever possible and make it a habit to manually check for updates on software that doesn’t update automatically. Keeping software current not only improves security but can also boost performance, fix bugs, and add new features.
Use reliable antivirus software
Antivirus software, sometimes called antimalware or antispyware software, can help detect and remove malware from your computer. It does this in two main ways: by comparing files to a database of known malware and by using advanced techniques like heuristic analysis that analyze suspicious behavior or patterns.
Most OSs come with built-in antivirus protection:
- Windows: Includes Microsoft Defender, which provides strong, real-time protection against most common threats.
- macOS: Features XProtect, Gatekeeper, and other built-in tools that automatically scan for malware and block unverified apps.
- ChromeOS: Uses sandboxing and automatic updates to isolate threats and protect the system without requiring separate antivirus software.
- Linux: Faces fewer traditional malware threats, but open-source tools like ClamAV can help detect infected files, especially when sharing data with Windows or macOS devices.
You may also consider a third-party antivirus tool for extra features like web protection, which blocks access to known malicious sites, or dark web monitoring, which alerts you if your personal information appears in a data breach. Keep in mind that you should avoid running more than one antivirus program at the same time, as this can cause conflicts or slow down your computer.
To get the most out of your antivirus software, keep it up to date so it can recognize the latest threats, enable real-time protection, and schedule regular full-system scans. Pay attention to any alerts or quarantine notices, and follow the recommended steps to resolve them right away.
Enable and customize firewall protection
A firewall acts as a barrier between your home computer and potentially harmful traffic from networks, including the internet. It monitors incoming and outgoing connections, allowing legitimate data to pass while blocking unauthorized access.
Most OSs come with built-in firewall protection, but it’s important to customize your firewall’s settings for optimal security. You can improve protection by allowing trusted programs to communicate while blocking unknown applications, configuring notifications for suspicious activity, and adjusting rules for different network types such as private or public connections.
Firewalls can also restrict or allow traffic based on properties like IP addresses, ports, or specific program paths, giving you finer control over what can access your computer.
Use strong, unique passwords and multi-factor authentication (MFA)
A strong password typically combines uppercase and lowercase letters, numbers, and symbols and avoids common words, sequential characters (like 1234 or abcd), repeated characters (like aaa111), or easily guessed personal information such as birthdays or names.
If you find it difficult to remember unique passwords for every account, using a password manager, like ExpressKeys, can help. These tools generate, store, and autofill complex passwords safely, reducing the temptation to reuse the same password across multiple accounts.
You can further strengthen any account’s security by enabling multi-factor authentication (MFA) or two-factor authentication (2FA). These features add extra verification steps, such as a code sent to your phone or generated by an authentication app, to confirm your identity when logging in. With MFA enabled, a threat actor might need your password, phone, and phone PIN to access your account.
Using MFA or 2FA does mean it’ll take a few extra seconds to log into your accounts, which can seem like a hassle, but it could save you a lot more trouble in the long run.
Back up your data safely
No matter how security-conscious you are, it’s still possible to suffer a malware infection that compromises your files, such as a ransomware attack. That's why it's important to regularly back up your data to ensure that you can recover important documents. Backing up your files also protects them from hardware failure or accidental deletion.
An effective backup strategy involves using more than one method, such as an external hard drive and cloud storage services, to create redundancy. This ensures that even if one backup method is compromised or fails, your important files remain protected and recoverable.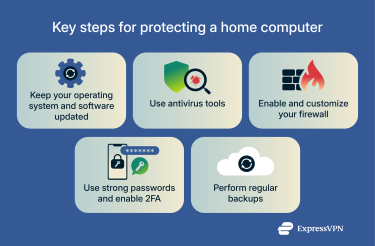
Cybersecurity awareness: Recognize and prevent threats
When it comes to cyber threats, awareness is your first line of defense. This is especially true because the leading cause of security breaches today isn’t technical vulnerabilities but social engineering, which occurs when a threat actor manipulates a victim into compromising their own security.
Understanding how common threats work and how to spot them helps you avoid risky situations and take swift action if something seems wrong.
Common cyber threats
Here are some common threats to home computers:
- Malicious attachments and downloads: Malware is often spread through infected email attachments in phishing emails or software from untrusted sources.
- Drive‑by downloads: Just visiting a malicious or compromised website can trigger an automatic download and install malware on your device.
- Infected removable media: USB drives or other external storage can carry malware that executes when files are opened.
- Password attacks: Attackers may try to guess or steal your computer’s local account passwords to gain unauthorized access, often using methods like brute-force attacks (when attackers systematically try thousands of password combinations using automated tools).
- Compromised devices on your network: If another device on your network is compromised, it can be used to access or infect other devices on the same network.
- Man-in-the-middle (MITM) attacks: If your home Wi‑Fi is insecure (weak password or outdated encryption), an attacker could intercept communications between your devices and the router, potentially capturing sensitive information or injecting malicious content.
Staying alert to these threats is just as important as following preventive steps. Even with strong defenses in place, cybercriminals constantly look for new ways to trick users or exploit overlooked weaknesses. Keep an eye out for unusual system behavior, unexpected messages, or anything that feels out of place, and act quickly by scanning your device or updating your security tools if something seems suspicious.
Stay informed: Best cybersecurity blogs and news sources
Following reliable cybersecurity sources keeps you up-to-date on emerging threats and helps you understand the latest protections. Besides the ExpressVPN blog, here are some trusted organizations and resources to follow:
- National Institute of Standards and Technology (NIST): A U.S. federal agency that develops cybersecurity standards and best-practice frameworks. Its blog and news releases cover security guidance, emerging risks, and practical tips for protecting devices and data.
- Cybersecurity and Infrastructure Security Agency (CISA): The U.S. government’s lead agency for cyber defense and critical infrastructure protection. CISA publishes alerts, guidance, and best practices useful for both organizations and individual home users.
- European Union Agency for Cybersecurity (ENISA): The EU’s agency for improving cyber resilience. ENISA provides threat reports, security guidance, and updates on major incidents, broadly relevant even outside Europe.
- Center for Internet Security (CIS): A nonprofit that develops recognized cybersecurity controls and benchmarks to help both individuals and organizations improve their security posture.
Free online tools to evaluate your security level
Here are some free tools you can use to check your system’s security and identify areas that may need improvement:
- Pentest-Tools.com: Offers a collection of free online vulnerability scanners and reconnaissance utilities (e.g., port scanning, website reconnaissance) that let you test your network or internet-connected devices for exposed services.
- Nmap: A well-known open-source network mapper and port scanner. While more technical, it can be used by home users to check which services or devices are running on their network and what might be exposed.
- OpenVAS (Community Edition / Free): An open-source vulnerability scanner that performs unauthenticated and authenticated scans of systems, services, and network devices with regularly updated vulnerability tests.
- ManageEngine Vulnerability Manager Plus (Free Edition): A free vulnerability scanner that detects software vulnerabilities, open ports, misconfigurations, and missing patches. It offers a user-friendly interface with dashboards to help non-experts see what needs attention.
Protecting your home network
Protecting your home computer isn’t just about securing your device; cybersecurity also includes network security. Every device you use, including your computer, phone, smart TV, and Internet of Things (IoT) gadgets, connects through your home network, so a weak network can expose all of them to attack. Thankfully, a few simple precautions can go a long way toward making your home network more secure.
Secure your Wi-Fi router
The most important step in securing your home network is making sure your Wi-Fi router is properly protected. Your router acts as the gateway between your devices and the internet, so vulnerabilities here can give attackers access to everything on your network.
Here are some key precautions you can take to protect your network.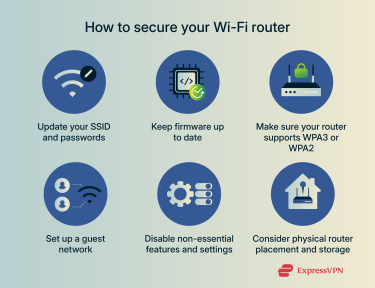
Update your default admin and Wi-Fi network passwords
Many routers come with default admin credentials (username and password) for accessing the router’s settings, and these are often really easy to guess. The default username and password for many routers may just be “admin” or something similar.
If someone can log into your router, they could change your Wi‑Fi password, open ports, monitor your network traffic, or even redirect your internet traffic to malicious sites.
It’s also important to use a strong, unique password for your Wi-Fi network because an unauthorized user could slow down your internet or try to access devices on your network, including your home computer.
Keep firmware up to date
Router updates often address security vulnerabilities that could be exploited by bad actors. We recommend enabling automatic updates if your router supports it.
Change the default SSID
The default Service Set Identifier (SSID), which is your Wi-Fi network’s name, can reveal your router type and give attackers clues about your devices. However, a personalized SSID may also reveal information about you.
A simple, generic name like “Wi-Fi” can be the safest choice for those who are very concerned about privacy. That’s because there are databases and tools that collect information about unique SSIDs and their locations. In rare cases, a unique network name could be used to help pinpoint your physical location, but for most people, this isn’t a common concern.
The most important step is to change the default SSID to something other than the factory name, whether that’s a unique name you like or a simple, generic one you prefer for privacy.
Make sure your router supports WPA3 or WPA2 encryption
Wi-Fi Protected Access (WPA) is a security standard that protects your wireless network by encrypting the data sent between your devices and your router. Encryption scrambles the data sent over your Wi‑Fi so that anyone listening can’t read it.
WPA3 is the latest and most secure option, and WPA2 with Advanced Encryption Standard (AES) is also considered safe for most home networks. Avoid older protocols like Wired Equivalent Privacy (WEP), WPA, or WPA2 with Temporal Key Integrity Protocol (TKIP), which are easy for attackers to break. If your router doesn’t support WPA3 or WPA2 AES, consider replacing it with a modern router that does.
Disable non-essential features/settings
Some routers include extra features that can increase your security risk. Consider disabling the following unless you specifically need them:
- Remote management: This feature allows you to access your router’s settings from anywhere over the internet, which can be convenient if you need to troubleshoot or configure your network while away from home. However, leaving it enabled also opens a door for attackers to try to access your router remotely.
- Wi-Fi Protected Setup (WPS): WPS simplifies device connections but is vulnerable to brute-force attacks and Pixie Dust hacks (a unique attack that tries to intercept your initial WPS handshake), which could allow an attacker to join the network without your Wi‑Fi password.
- Universal Plug and Play (UPnP): UPnP lets devices on your network find and connect to each other automatically, which is convenient for setup. However, malware or attackers can exploit it to bypass your firewall, control devices remotely, or spread across your network.
Additionally, if you’re ever away for extended periods or don’t need internet access, you should consider disabling your Wi-Fi entirely. This prevents outsiders from attempting to access your network. Some routers let you set a schedule to automatically turn Wi-Fi on and off.
Consider physical router placement and storage
Anyone with physical access can reset the router and use default credentials to access your network. Keep it out of public or easily reachable areas.
Set up a guest Wi-Fi network
A guest Wi-Fi network is a separate network with its own strong password for visitors or devices that only need internet access, like smart home gadgets. This isolates them from your main devices and reduces security risks.
Monitor connected devices
It’s a good idea to regularly check which devices are connected to your network and remove any you don’t recognize. This helps detect unauthorized access to your network early.
Reduce Wi-Fi signal range
Wi‑Fi signals can extend beyond your home, which means someone nearby could potentially intercept your network traffic or attempt to access your network. By adjusting router placement, antenna direction, and transmission power, you can try to limit coverage to your home.
Use a VPN for added privacy and safety
Using a virtual private network (VPN) on your home computer adds an extra layer of security against network-based threats by encrypting your internet traffic as it travels from your device to the VPN server. This prevents bad actors on your local network or your ISP from seeing which websites you visit or intercepting unencrypted data.
VPNs also mask your IP address from the sites and services you access. This can reduce certain risks, such as targeted network attacks or tracking based on your IP address. For the best privacy, choose a reputable VPN provider with a strict no-logs policy.
Additionally, you can install a VPN on your router to secure all devices connected to your home network, reducing the risk of attackers moving laterally from one compromised device to others.
Some VPNs include extra security features as well. ExpressVPN offers Threat Manager, which can protect your online traffic from malicious websites and trackers, and Identity Defender (available to U.S. users on select subscriptions), which includes dark web monitoring, credit monitoring, and other identity theft protection tools.
Note that using a VPN doesn’t make your device unreachable or immune to malware or phishing, and it doesn’t replace antivirus software. For maximum security, it’s a good idea to use both.
FAQ: Common questions about protecting home computers
How can I protect my personal computer most effectively?
Here are some simple steps to secure your home computer: install reputable antivirus software, enable and customize your firewall, use strong, unique passwords for all of your accounts, and keep your OS and software up to date. You should also take steps to protect your home network by securing your Wi-Fi router and installing a VPN.
What antivirus software is best for home use?
There’s no single “best” antivirus; most programs provide similar core protections and will strengthen your computer’s defenses against malware. The main factors that differentiate them are their extra features, cost, and compatibility. The most important thing is to choose trusted software by checking recommendations from reputable cybersecurity sources.
How can I secure my Wi-Fi network?
To secure your home network, we recommend that you use strong, unique passwords for your router and Wi‑Fi network, keep your router firmware up to date, and enable Wi-Fi Protected Access 3 (WPA3) or WPA2 Advanced Encryption Standard (AES) encryption. You should also disable risky features like Wi-Fi Protected Setup (WPS), Universal Plug and Play (UPnP), and remote management, and set up a separate guest network for visitors or smart devices.
What is MFA, and why is it important?
Multi-factor authentication (MFA) protects your accounts by adding extra verification steps. This means that even if someone knows your password, they still need one or more “factors,” such as a code from your phone or an authentication app, to access your accounts.
How often should I back up or update my software?
There’s no one-size-fits-all answer for how frequently you should back up your files. It depends on how often you modify your files and how important those changes are. On the other hand, you should update your software regularly, ideally as soon as updates are available. This is because software updates often address security vulnerabilities that attackers could exploit.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN